Introduction
Cloud security testing is a form of safety testing approach used to evaluate the safety of cloud infrastructure, figuring out risks and vulnerabilities that could be exploited via hackers. By leveraging security testing services, the primary aim is to ensure that the cloud surroundings can efficiently shield an organization's personal data.
Cloud protection emphasizes the integration of policies, approaches, and technology to make sure data protection, help regulatory compliance, and provide control over privacy, access, and authentication for customers and gadgets.
Table of Contents
- What is Cloud Security Testing?
- Why Do You Need Cloud Security Testing?
- What Are the Main Threats Affecting Cloud Security?
- Effective Cloud Security Testing Checklist
- What are the Types of Cloud Security Testing?
- Advantages of Cloud Security Testing
- Disadvantages of Cloud Security Testing
- Conclusion
What is Cloud Security Testing?
This form of protection checking out technique in which cloud infrastructure is tested for protection risks and loopholes that hackers can make the most and the primary intention. It is to make certain the safety measures are strong enough and locate any vulnerable spots that hackers ought to make the most.
The cloud security testing form of trying out examines a cloud infrastructure, company’s security policies, controls, and strategies. It tries to find vulnerabilities that might cause information breaches or safety issues. Cloud-based application security testing is often performed by third-party auditors working with a cloud infrastructure provider, but the cloud infrastructure provider can also perform it.
Security specialists perform cloud security testing using a variety of manual and automated testing methodologies. The data generated by this testing type can be used as input for an audit or review. Not only this, but cloud security testing can also provide in-depth analysis and the risk posture of the security risks of cloud infrastructure.
Why Do You Need Cloud Security Testing?
Securing cloud environments isn't a mere extension of traditional security practices; it demands reimagining security strategies from the ground up. The nature of the cloud introduces complexities that require novel approaches.
In the conventional on-premises setup, security measures often revolve around the perimeter defense strategy, where robust firewalls and network security mechanisms guard against external threats. However, the lines between internal and external networks are blurred in the cloud. Virtualized resources, multi-tenant environments, and dynamic workloads challenge the very notion of a traditional perimeter.
Moreover, the cloud encourages a DevOps culture of rapid development, deployment, and continuous integration. While this approach fosters agility, it can inadvertently lead to security gaps if not vigilantly managed. The rapid pace of change in cloud environments necessitates security measures that are not just static but adaptive and responsive.
What Are the Main Threats Affecting Cloud Security?
- Insecure APIs: Insecure APIs pave a treacherous path, often culminating in large-scale data breaches reminiscent of incidents involving Venmo and Airtel.
- Server Misconfigurations: Blunders in cloud server configurations, encompassing permissions, data encryption, and segregating public and private data, constitute a gateway for nefarious infiltration.
- old software program: A cause, ranging from disjointed update methods by means of providers to consumer-initiated disabling of automated updates, ushers in a generation of previous software ripe for exploitation.
- Insecure Coding: A landscape riddled with insects, starting from square injection (SQLi) to go-website scripting (XSS) and go-web page request forgery (CSRF).
- Malware: Malicious software program can scouse borrow information, wreak havoc on our structures, and disrupt operations.
- Data Loss: Losing vital data, especially if it involves customer information. A slippery slope can lead to serious consequences, affecting the bottom line and customer trust.
- Insufficient Identity and Access Management Practices: Crafting a robust identity and access management system forms a critical layer of defense, ensuring only authorized personnel gain entry.
Effective Cloud Security Testing Checklist
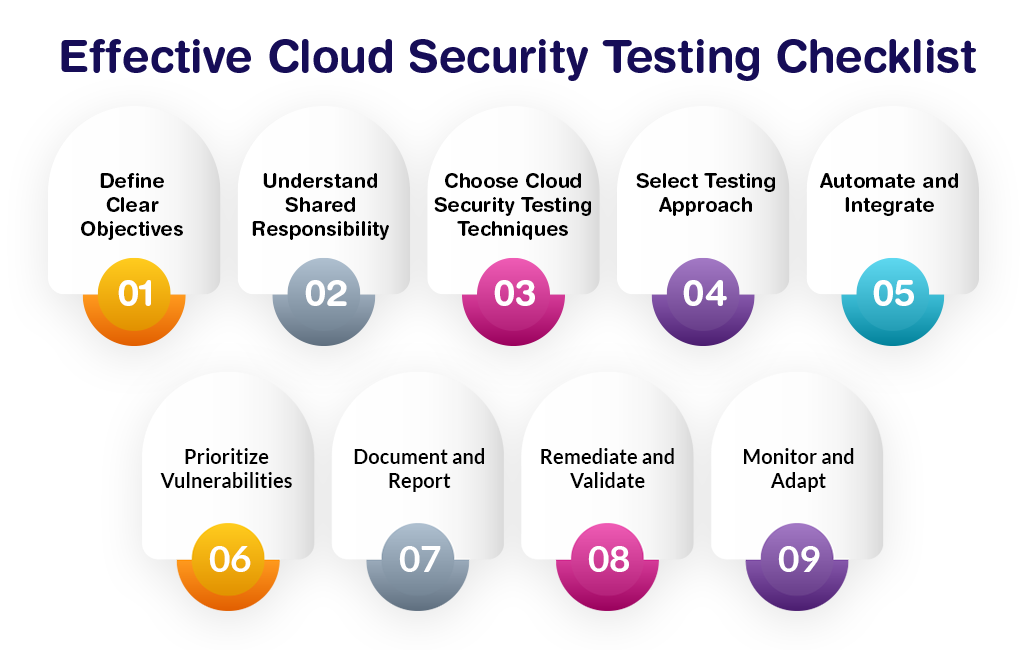
Step 1. Define Clear Objectives
Define a clear vision for your cloud security testing efforts. Establish specific security goals that align with your organization's overall security strategy. You can use existing security frameworks or standards like OWASP SAMM, AWS CIS, etc. to simplify the planning of mitigation measures implementation and progress tracking. Identify the scope of testing, including cloud assets, applications, and data to be evaluated. Set boundaries for the testing to ensure comprehensive coverage.
Step 2. Understand Shared Responsibility
Engage with your cloud service provider to thoroughly understand their shared responsibility model. Clarify security responsibilities to avoid gaps or overlaps. Define roles and responsibilities within your organization for cloud security testing. Establish oversight mechanisms to ensure compliance with security practices.
Step 3. Choose Cloud Security Testing Technique
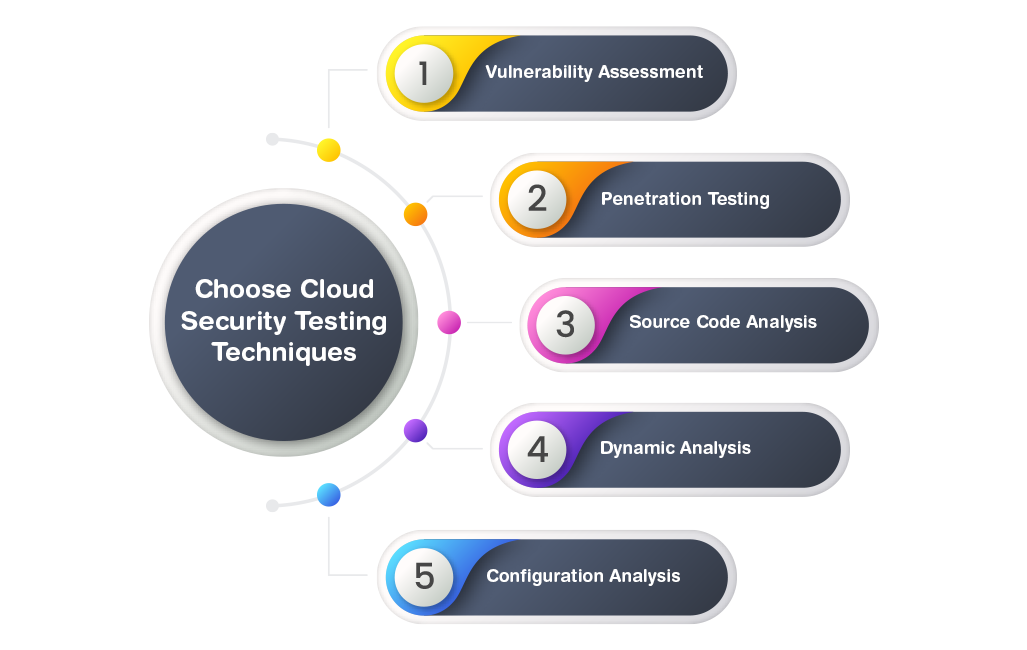
Vulnerability assessment: Leverage computerized tools to become aware of regarded vulnerabilities to your cloud packages and infrastructure. Prioritize vulnerabilities primarily based on severity and relevance. Through automated scans, it identifies recognized safety loopholes, misconfigurations, and susceptible factors. With the aid of spotlighting those hidden weaknesses, vulnerability assessment equips you with insights to enhance your defenses, proactively decreasing the chance of breaches.
Penetration Testing: Behavior-managed simulated assaults to assess your cloud environment's susceptibility to exploitation. By means of simulating intrusions, cloud penetration testing services reveal vulnerabilities that malicious actors could exploit. Uncover capacity access points, vulnerable authentication mechanisms, and different gaps to your defense.
Source Code Analysis: evaluation of the source code of cloud programs to discover coding vulnerabilities and protection flaws. Integrate cozy coding practices into the improvement lifecycle. This technique offers a granular examination of the software's structure, pinpointing regions liable to injection assaults, bypass web page scripting, and distinct vulnerabilities.
Dynamic Analysis: Discover vulnerabilities that would best occur at some stage in actual utilization. Also, discover unauthorized get admission to try, records leaks, and other anomalies in real-time, permitting rapid responses to potential threats.
Configuration Analysis: Identifies open ports, weak admission to controls, and other configuration errors that could disclose your structures to breaches. Toughen your protection posture by way of stopping unintended vulnerabilities.
Step 4: Select Testing Approach
Black Box Testing: Simulate real-world attacks without prior knowledge of the cloud environment. This approach tests the effectiveness of external security defenses and the organization's incident response. However, the limitations are apparent – testers lack contextual understanding and might miss intricate flaws.
Gray Box Testing: Combine elements of both Black Box and White Box testing. Limited information about the cloud environment is provided, enabling testers to emulate insider threats. This approach marries the advantages of both black and white box testing. QA engineers possess sufficient insights to navigate the cloud landscape effectively while retaining an element of realism. Gray box testing excels when fine-tuning is crucial, especially in complex setups where excessive access might disrupt normal operations.
White Box Testing: Involves deep knowledge of the cloud infrastructure and applications. Testers can comprehensively assess security controls and uncover vulnerabilities. The advantage here is precision – testers can identify vulnerabilities with unparalleled accuracy. However, the limitation lies in its potential lack of real-world relevance, as security teams might approach challenges differently from hackers. White box testing thrives in scenarios demanding meticulous analysis, making it ideal for critical cloud systems where accuracy is paramount.
Step 5. Automate and Integrate
Integrate automation tools for continuous security testing. Automated vulnerability scans, code analysis, and security checks to ensure consistent coverage and timely feedback. Embed security testing into your CI/CD pipelines to identify vulnerabilities early in development.
Step 6. Prioritize Vulnerabilities
Develop a risk-scoring mechanism to prioritize vulnerabilities based on their potential impact and exploitability. Consider factors such as asset criticality and data sensitivity. Create threat models to understand potential attack scenarios and their consequences. Align threat models with cloud-specific risks to tailor testing efforts.
Step 7. Document and Report
Document findings, including identified vulnerabilities, misconfigurations, and potential exploits. Provide clear and actionable recommendations for remediation. Prepare executive-level summaries communicating testing results, risk levels, and potential business impacts.
Step 8. Remediate and Validate
Prioritize and address vulnerabilities promptly to reduce the window of exposure. Collaborate with development teams to implement effective fixes and patches. Validate the effectiveness of remediation efforts through thorough retesting. Ensure that vulnerabilities have been successfully mitigated without introducing new issues.
Step 9. Monitor and Adapt
Implement continuous monitoring mechanisms to detect and respond to evolving threats and vulnerabilities. Utilize intrusion detection systems, log analysis, and threat intelligence. Integrate threat intelligence feeds to stay informed about emerging cloud-specific threats and attack patterns. Adapt testing strategies based on evolving risks.
What are the Types of Cloud Security Testing?
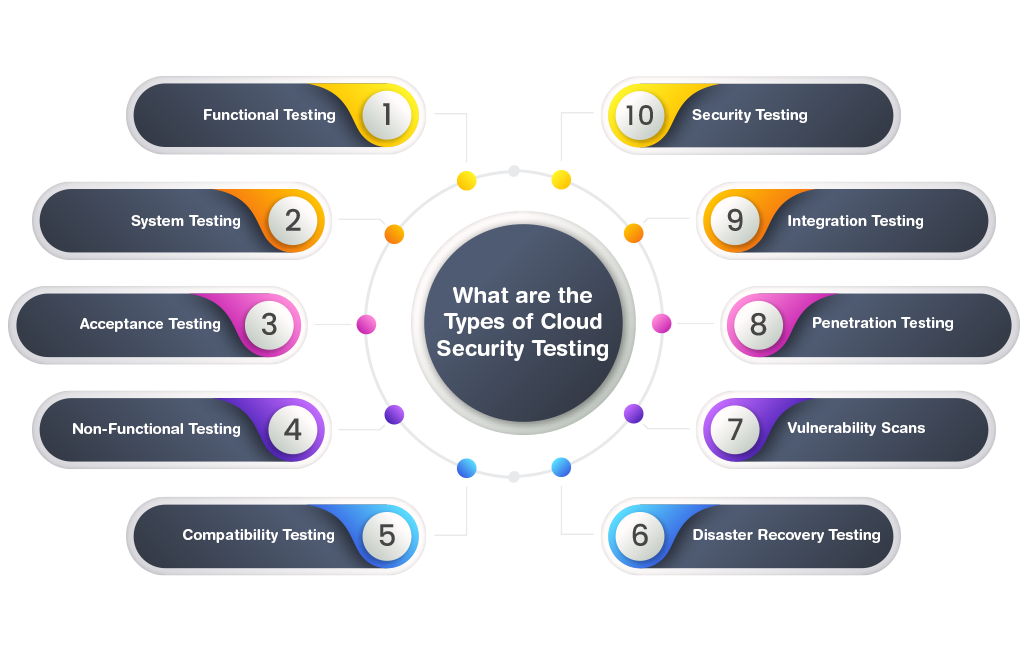
1. Functional Testing
It is a test of your application's performance against user expectations. By meticulously evaluating each function about predefined requirements, you ensure that your software delivers the intended outcomes. This technique guarantees that your application functions and provides a seamless and satisfying user journey.
2. System Testing
It is a panoramic view of the software universe, navigates beyond isolated elements. This technique traverses the entire expanse, holistically evaluating requirements and functionalities.
3. Acceptance Testing
This type of testing is your assurance that your chosen cloud solution is in sync with your business requirements. It's like the final stamp of approval that your software aligns with your organizational objectives.
4. Non-Functional Testing
Beyond functionality lies non-functional testing, where the spotlight shines on an immersive user experience. Quality of service, reliability, usability, and swift response times are meticulously assessed, weaving a tapestry that exudes excellence.
5. Compatibility Testing
Compatibility testing, an exquisite orchestration, orchestrates an enchanting symphony between software and its varied environments. It delicately ensures that the software dances gracefully across diverse cloud landscapes and operating systems.
6. Disaster Recovery Testing
Disaster recovery testing, a sentinel of continuity, assesses the application's resilience in adversity. It masterfully evaluates recovery time, ensuring that the application's revival, with minimal data loss, remains a swift reality.
7. Vulnerability Scans
Imagine vulnerability scans as vigilant guards equipped with automated tools. Their task is to meticulously comb through an organization's systems and data, seeking out familiar vulnerabilities. These scans offer valuable insights, spotlighting potential weak spots.
8. Penetration Testing
Picture penetration tests as audacious explorers charting uncharted territories. Conducted by ethical hackers, they simulate determined intrusion attempts into an organization's systems. The goal is to unearth hidden vulnerabilities, providing a genuine gauge of security readiness.
9. Integration Testing
This technique exposes any potential flaws that may arise when different components join forces. Integration testing ensures a well-coordinated software ecosystem by testing how these modules communicate and collaborate.
10. Security Testing
Ordinary protection checking out is like fortifying the walls of a fortress to keep out intruders. It guarantees that your software program is resilient in opposition to capacity threats and vulnerabilities. From simulating assaults to automated scans, security is trying to guard your application's integrity and consumer data.
Advantages of Cloud Security Testing
1. Enhanced Security Posture
Proactive risk identification: Trying out can uncover vulnerabilities earlier than attackers do, permitting corporations to address troubles before they are exploited.
Compliance guarantee: Ordinary checking out enables ensuring that cloud environments comply with relevant rules and standards (e.g., GDPR, HIPAA)
2. Risk Management
Mitigating risks: Identifying and addressing vulnerabilities reduces the risk of information breaches and cyberattacks.
Incident reaction Readiness: Checking out allows an organization's capacity to respond to safety incidents effectively.
3. Continuous Improvement
Security Best Practices: Everyday testing promotes adherence to security-first practices and non-stop development of security measures.
Adaptation to Changes: It helps organizations adapt to new threats and modifications in the cloud environment, including updates to cloud offerings or infrastructure.
4. Visibility and Control
Insight into Cloud Environment: Offers visibility into the security posture of cloud sources and configurations.
Control Over Security Measures: Enables organizations to make certain that their protection controls are effective and functioning as supposed.
5. Customer and Stakeholder Trust
Building Confidence: Demonstrating a commitment to cloud protection through regular trying out can construct trust with clients and stakeholders.
Market Advantage: A sturdy security posture may be a competitive benefit within the market.
Disadvantages of Cloud Security Testing
1. Cost and Resource Intensive
Financial Cost: Cloud safety testing can be steeply priced, especially for small to medium-sized corporations.
Resource Allocation: Calls for devoted time and understanding, that can pressure internal sources or necessitate hiring external specialists.
2. Complexity
Cloud Environment Complexity: Checking out may be difficult due to the complexity and dynamic nature of cloud environments, consisting of more than one layer of services and configurations.
Tool Limitations: The Gear used for trying out won't absolutely cover all components of cloud safety or might also have limitations specific to sure cloud companies.
3. False Positives/Negatives
Accuracy Issues: Safety testing gear would possibly generate false positives (incorrectly identifying a trouble) or fake negatives (failing to become aware of an actual difficulty), which may affect the reliability of the outcomes.
Overlooked Issues: A few vulnerabilities won't be detected because of boundaries in testing methodologies or equipment.
4. Disruption to Services
Testing Impact: A few kinds of safety checks, along with penetration testing, can probably disrupt cloud offerings or affect performance.
Operational Risks: There is a chance of affecting the stability of the cloud environment if testing is not carried out carefully.
5. Dependency on Cloud Providers
Limited Visibility: Cloud carriers typically control the underlying infrastructure, which may additionally restrict the visibility and control agencies have over sure security elements.
Provider-Specific Issues: Safety trying out might be tormented by the specific capabilities and configurations of different cloud vendors requiring specialized understanding.
Conclusion
Adopting Cloud security testing services is a crucial part of maintaining a cloud-based business and should be done regularly to ensure the security of cloud applications and infrastructure. A trusted software testing company can help organizations protect their data, applications, and infrastructure from cyber threats and comply with industry and government regulations.
About Author
 Ashok Makwana is a seasoned Quality Assurance professional with a passion for continuous learning. He started his journey as a QA in September 2020 and embraced challenges as opportunities for growth. His drive to excel led him to aspire to become a Lead QA Manager, exemplifying dedication and expertise in his field. With a proactive approach and a thirst for knowledge, Ashok Makwana embodies the spirit of lifelong learning and achievement in quality assurance.
Ashok Makwana is a seasoned Quality Assurance professional with a passion for continuous learning. He started his journey as a QA in September 2020 and embraced challenges as opportunities for growth. His drive to excel led him to aspire to become a Lead QA Manager, exemplifying dedication and expertise in his field. With a proactive approach and a thirst for knowledge, Ashok Makwana embodies the spirit of lifelong learning and achievement in quality assurance.


