
Table of Contents
Introduction to Nmap
Network Mapper (Nmap) is a network checking and host detection tool that's very valuable amid a few steps of penetration testing. Nmap isn't restricted to just gathering data and identification, it is additionally a powerful utility that can be utilized as a powerless detector or a security scanner. As part of security testing services, it serves as a multipurpose tool, and it can be run on numerous diverse operating systems including Windows, Linux, BSD, and Mac. Nmap can be used to detect:
- Live hosts present on the network (host discovery)
- Open ports on a host (port discovery or enumeration)
- Software and its respective port assigned to the service (service discovery)
- Operating system, hardware address, and the software version
- Vulnerabilities and security holes using Nmap scripts
The usage of Nmap depends on the target machine and the differences between simple (basic) scanning and advanced scanning. What follows are examples of some basic commands and their usage. In part II of this lab, more advanced Nmap scanning techniques are shown.
Basic Commands and Usage
In this case, we are scanning a single IP address of 192.168.225.138. You'll be able find the IP address of your host machine by typing IFCONFIG at the terminal prompt. This will show you your assigned IP address. You can then substitute the default IP address used in the lab with the IP address of your machine for scanning a single host.
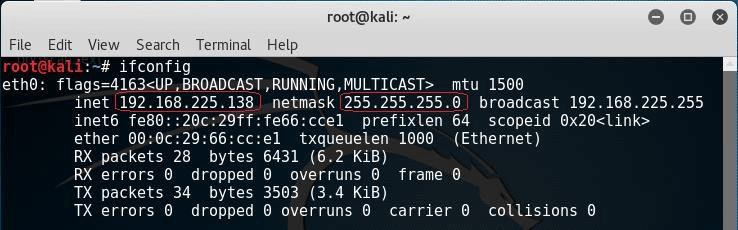
- Your IP address: In the above image, eth0 interface has been assigned the IP address of 192.168.225.138. This is my IP address; yours will differ!
- Network portion of your IP: For any class C, it is the first three octets 192.168.225.x The x in the last octet represents the IP address assigned to the host.
- Your subnet mask: My subnet mask is 255.255.255.0 since my network is a default class C network.
To scan a single system use:
# nmap 192.168.225.1
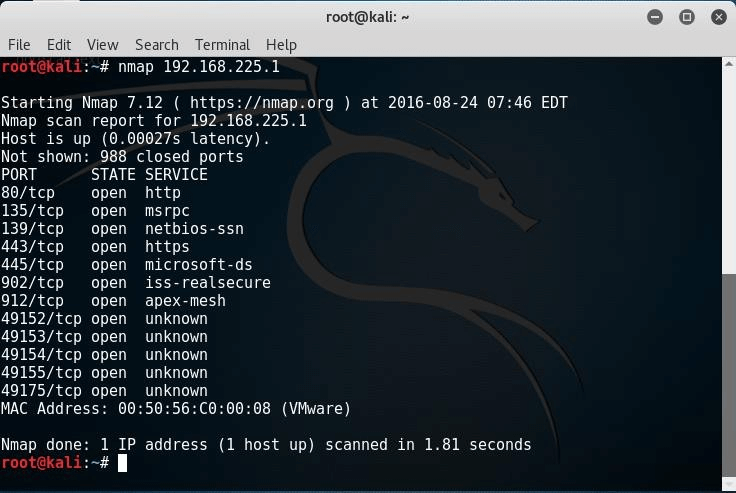
In this following illustration, we'll check a whole class C subnet starting with the primary accessible IP of 192.168.1.225.1 The /24 is CIDR shorthand that tells Nmap to check for all accessible IP addresses.
To scan the entire subnet use:
# nmap 192.168.225.1/24

The previous command will discover all the host that resides on your network.
To scan multiple targets, separate each target with a single space:
# nmap 192.168.225.1 192.168.225.8
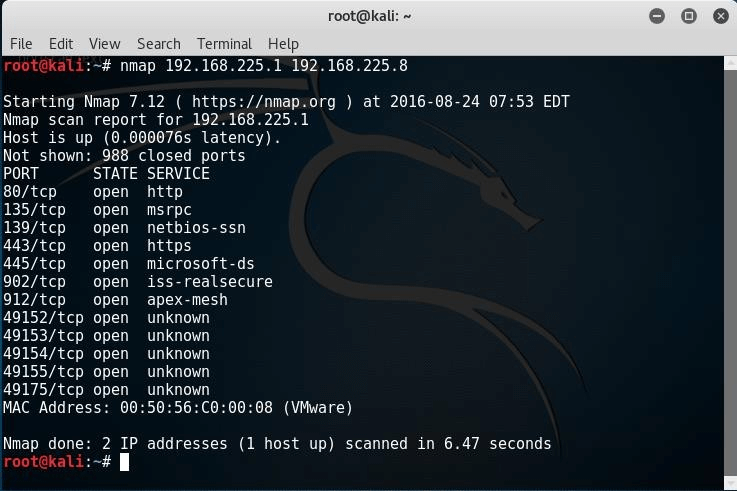
Using the previous command, I've scanned only two hosts with an IP address of 192.168.225.1 and 192.168.225.8
If you want to scan a range of IP addresses, but not the entire subnet, use this command:
# nmap 192.168.225.1-100
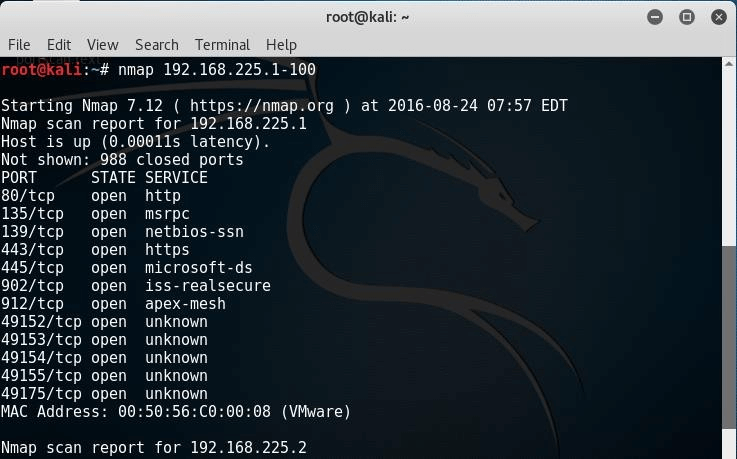
The previous command will scan for hosts with a starting IP address of 1 and end in 100.
Add the -sL option to view the list of all the hosts you have currently scanning:
# nmap -sL 192.168.225.1/24
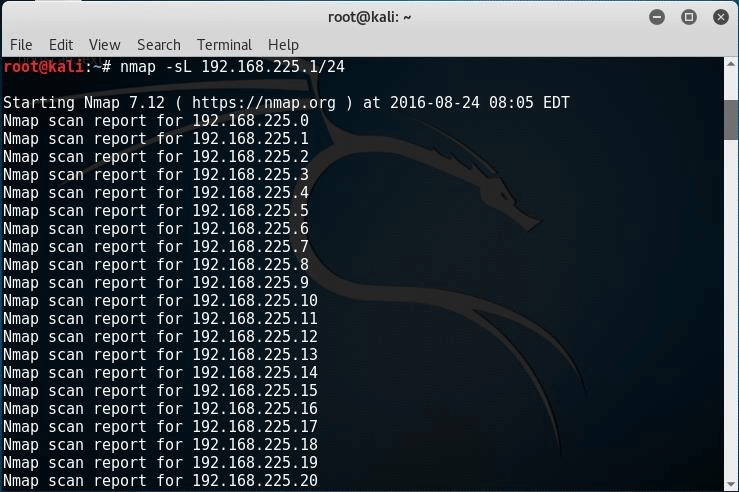
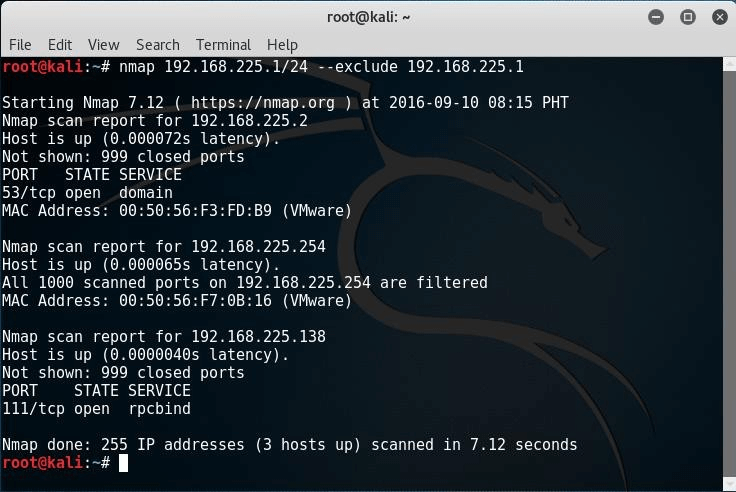
In some cases, we might need to exclude or exempt an IP from the scan. We can use the exclude parameter:
# nmap 192.168.225.1/24 - -exclude 192.168.225.1
We scan for specific ports such as HTTP, FTP, and Telnet port by using the Nmap parameter -p:
# nmap -p80,21,23 192.168.225.1
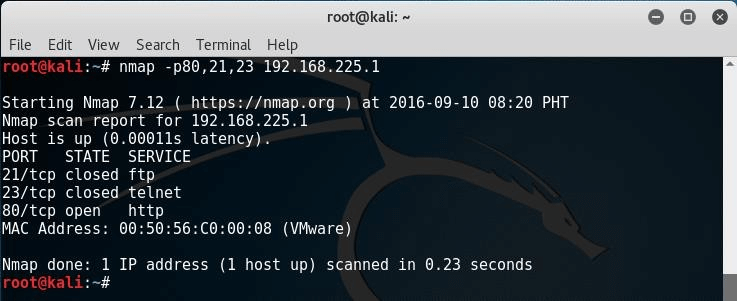
Replace the default IP address of 192.168.225.1 with the actual IP of any target machine which is part of your network. Scan the IP for ports 80, 21 and 23.
Your results will differ from those in the following image. This is only an example of what you might see.
Service and Open Port scan
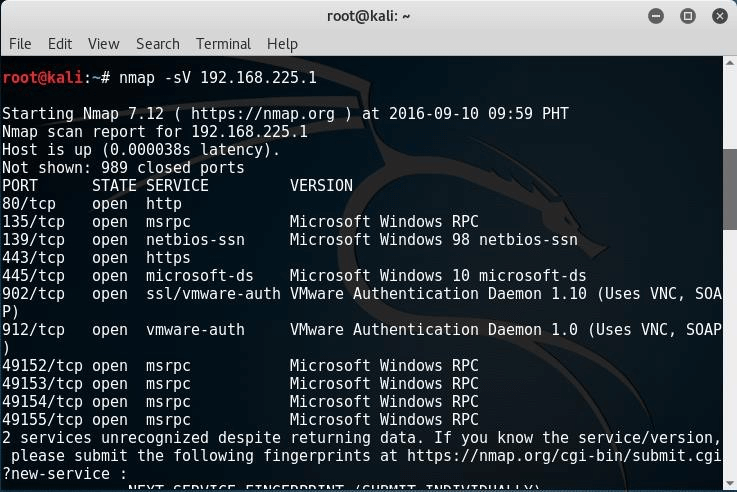
Version Detection (-sV): Version detection is the technique used to find out what software version is running on the target computer and on the respective ports. It is unlike the other scanning techniques because it is not used to detect the open ports, but it requires the information from open ports to detect the software version. In the first step of this scan technique, version detection uses the TCP SYN scan to find out which ports are open.
# nmap -sV 192.168.225.1

OS Detection
One of the foremost critical highlights that Nmap has is the capacity to distinguish remote operating systems and software. It is exceptionally accommodating during a penetration test to know about the operating system and the software used by the remote computer since you'll effectively anticipate the known vulnerabilities from this information.
Nmap has a database called nmap-os-db, the database contains information on more than 2,600 operating systems. Nmap sends TCP and UDP packets to the target machine and then it examines the response by comparing the result with the database. The Nmap operating system discovery technique is slightly slower than the scanning techniques because OS detection involves the process of finding open ports.
The example above clearly demonstrates that the Nmap first discovers the open ports, then it sends the packets to discover the remote operating system. The OS detection parameter is -O (capital O).
# nmap -O 192.168.225.1
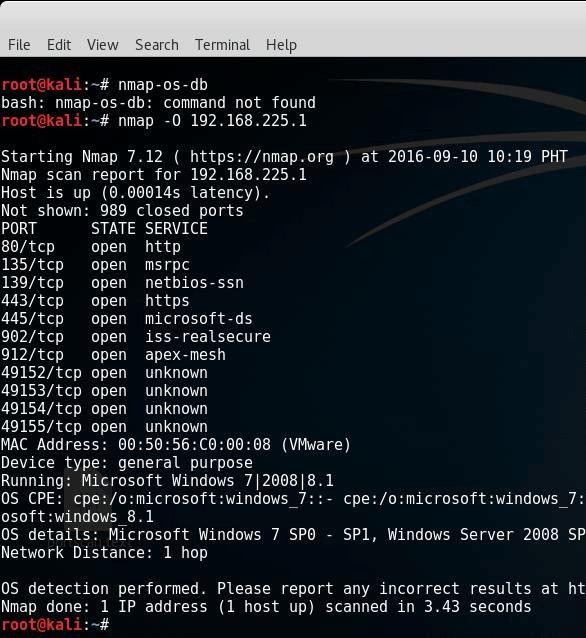
Nmap OS fingerprinting technique discovers:
- Device type (router, workstation, etc.)
- Running operating system
- OS details (the name and the version of OS)
- Network distance (the distance in hops between the target and attacker)
Suppose the target machine has a firewall, IDS, and IPS all enabled. You can use the command - PN to ensure that you do not ping to find the remote operating system. The -PN tells Nmap not to ping the remote computer since sometimes firewalls block the request.
# nmap -O -PN 192.168.225.1/24
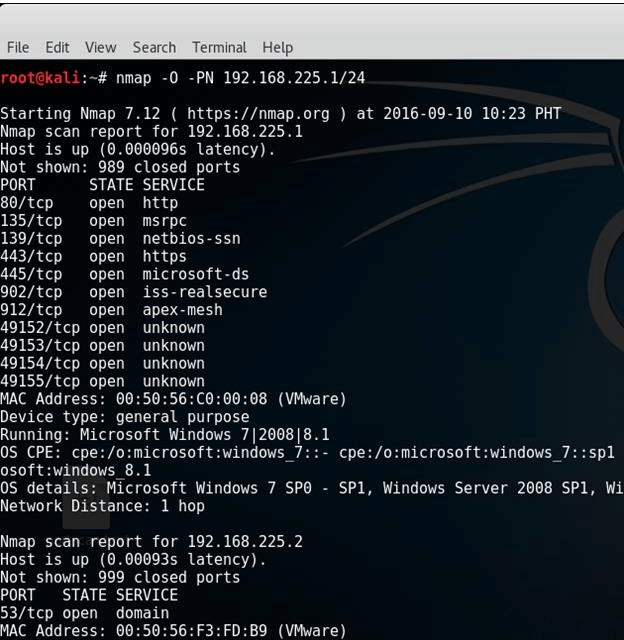
The command assumes every host on the network is alive so there is no need to send a ping request as. We bypass the ping request and go straight to discovering the operating system.
The Nmap OS detection technique works on an open and closed port. If Nmap fails to discover the open and closed port, then it gives the error:
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
This is an undesirable situation, and it is good to limit the operating system scans if Nmap is not sure about the OS. If Nmap is not sure about the OS, then there is no need to detect by using -- osscan_limit.
If it is difficult for Nmap to detect the remote OS accurately, you have the option of using Nmap’s guess feature: --osscan-guess finds the nearest match of the target operating system.
# nmap -O --osscan-guess 192.168.225.1/24
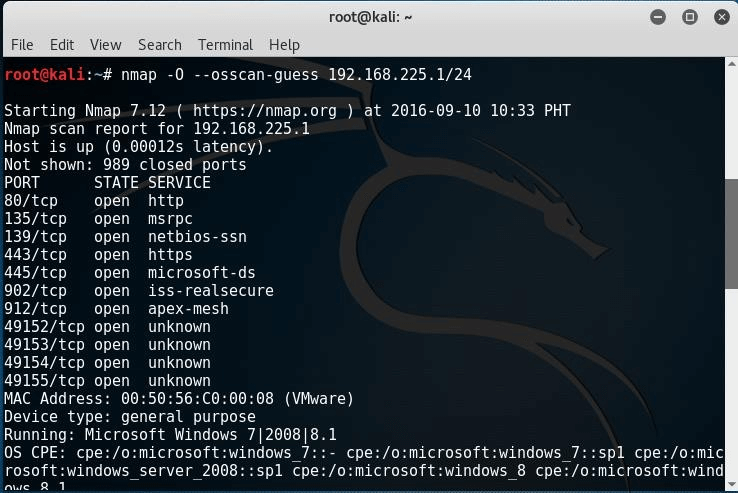
Replace the IP with that of a target machine running on your virtual network.
Conclusion
Nmap is an essential tool for network scanning and host detection. It helps security professionals identify live hosts, open ports, software versions, and remote operating systems. With its versatile scanning capabilities and scripting engine, it is indispensable for securing networks and identifying vulnerabilities before they can be exploited.
In the realm of cybersecurity, having robust security testing services is crucial. Hire excellent services from PixelQA and leverage tools like Nmap effectively to fortify your network defenses and safeguard your systems against potential threats.
About Author
Started his journey as a software tester in 2020, Rahul Patel has progressed to the position of Associate QA Team Lead" at PixelQA a Software Testing Company.
He intends to take on more responsibilities and leadership roles and wants to stay at the forefront by adapting to the latest QA and testing practices.
