Dynamic processes in Form-based authentication with OWASP ZAP are crucial for enhancing cybersecurity by continuously adapting to evolving threats, ensuring robust protection for applications. This approach enables real-time security adjustments, fortifying defenses against potential vulnerabilities and ensuring a resilient authentication system. As part of comprehensive Security Testing Services, OWASP ZAP's dynamic processes elevate security measures, providing a proactive and adaptive shield against emerging cyber threats.
In this post, we’ll unravel the intricacies of a process that goes beyond the basics, delving into the practical implementation of security measures. So, without any further ado, let's get started!
Table of Contents
- What is Dynamic application security testing?
- Different Modes of Attack
- Authenticated Scan Using ZAP
- Conclusion
What is Dynamic application security testing?
The process of simulating attacks on an application to find vulnerabilities is known as dynamic application security testing or DAST. This method is different from static application security testing (SAST), which looks for potential bugs, security flaws, and code smells in an application by examining its source code, configuration files, and infrastructure configuration. Finding these problems early in the software development life cycle is the main goal of SAST, as it prevents them from being exploited in a production setting. Creating scripts to examine the application's code and find vulnerabilities is a common step in SAST.
Different Modes of Attack
There are four types of modes you can see in the drop-down menu, at the top left side of the tool.
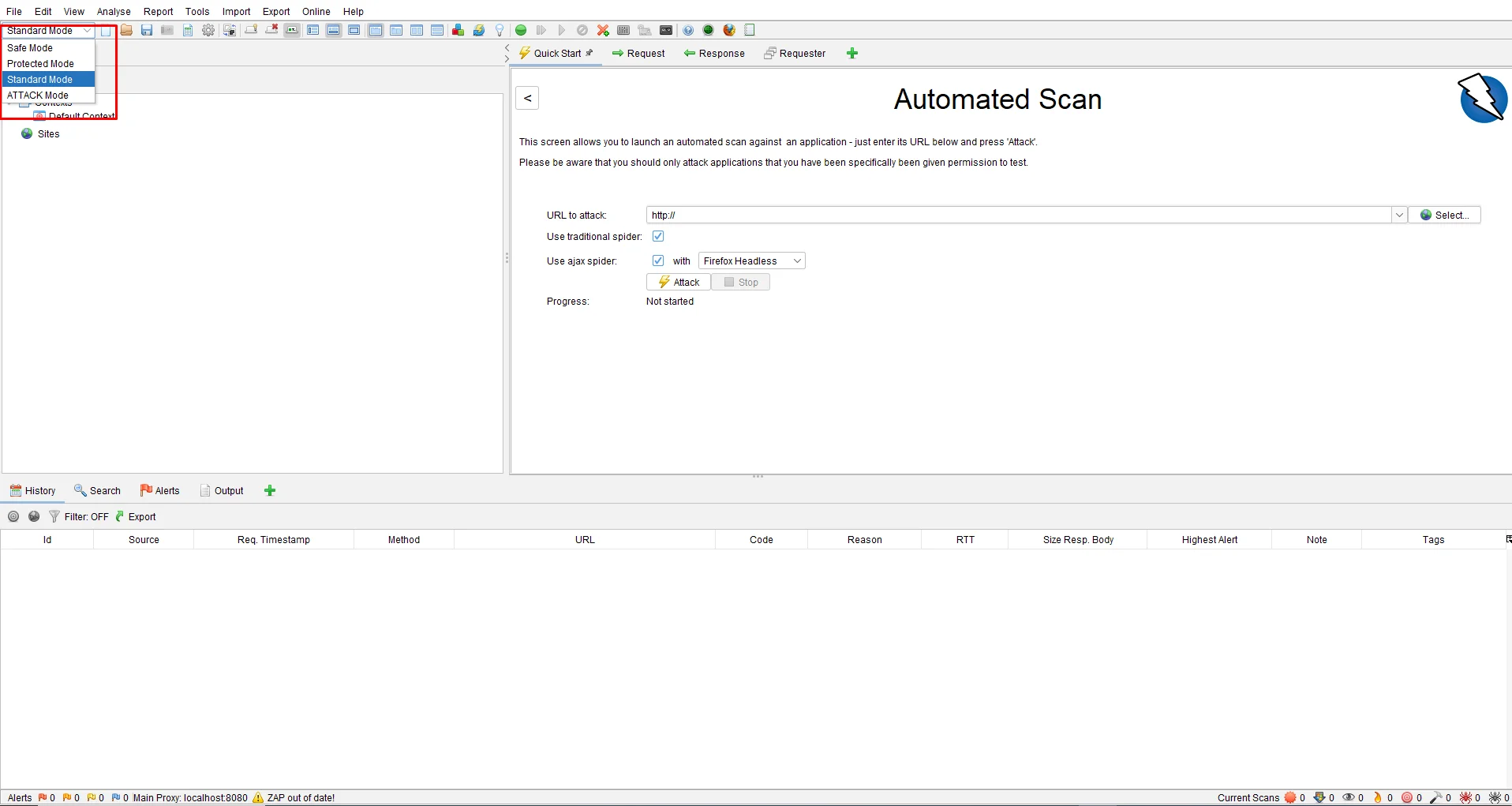
- Standard Mode: This allows you to do anything to your site.
- Safe Mode: This mode turns off all the dangerous features while scanning. This mode prevents the user from doing anything that is possible.
- Protected Mode: Allows users to scan the site in a particular scope. Harmful actions can only be performed in the sites mentioned in the scope.
- ATTACK Mode: New nodes are Actively Scanned when founded.
Authenticated Scan Using ZAP
An authenticated security scan is vulnerability testing performed by a logged-in user (Authenticated User) to determine the security of the network from an inside vantage point.
Crawl the Browser
To crawl your site, you can either use the default browsers provided by ZAP by clicking on the options at the top of the toolbox.
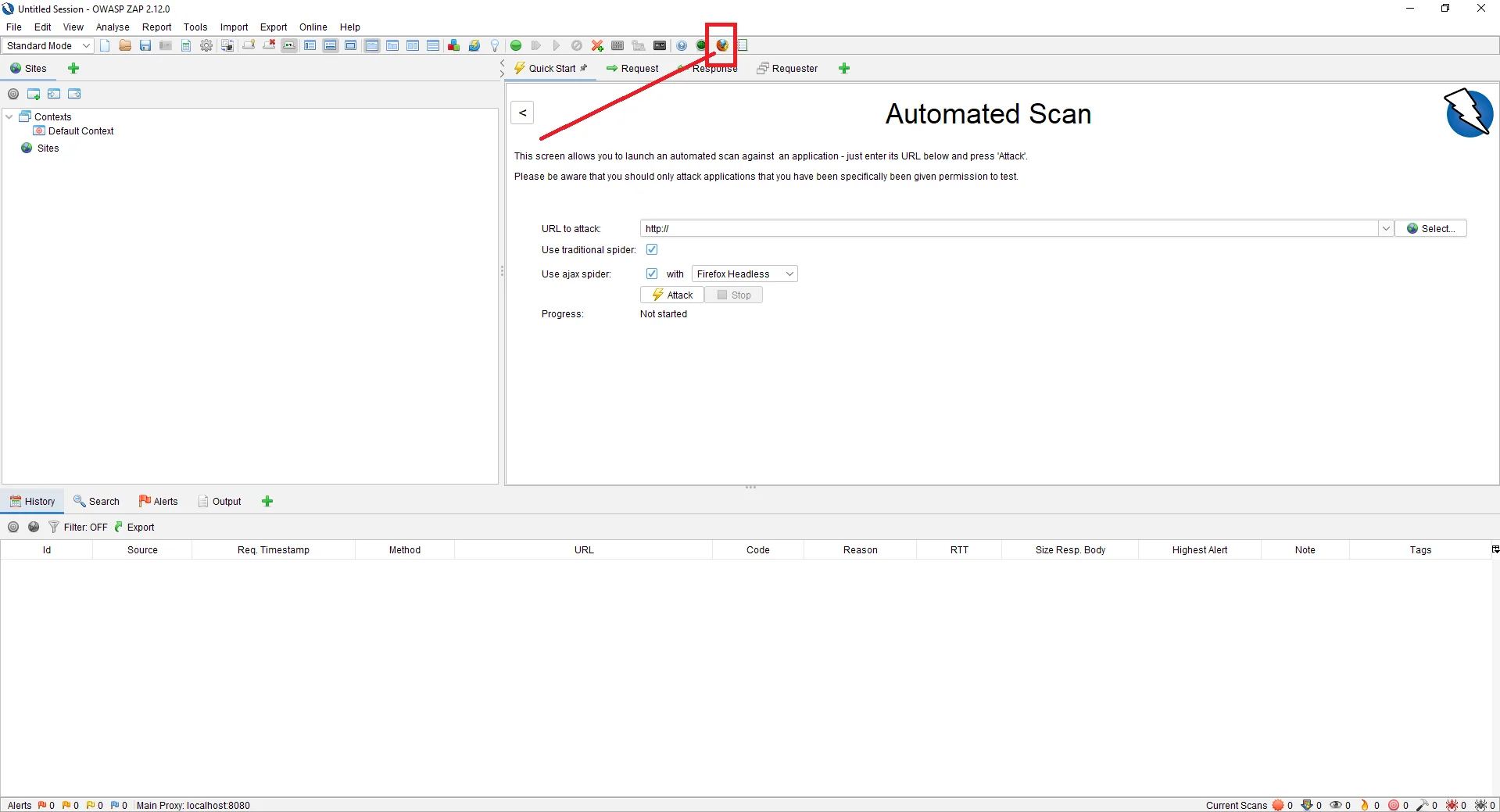
Or you can also use any other browser for that please follow the following steps.
Browser -> Options -> Advanced tab -> Network -> Settings -> Select Manual Proxy configuration — HTTP Proxy = 127.0.0.1 Port = 8080.
Then, open the browser and hit the URL of the site you are about to attack or scan. The more you crawl through your site, the more ZAP will be able to collect URLs
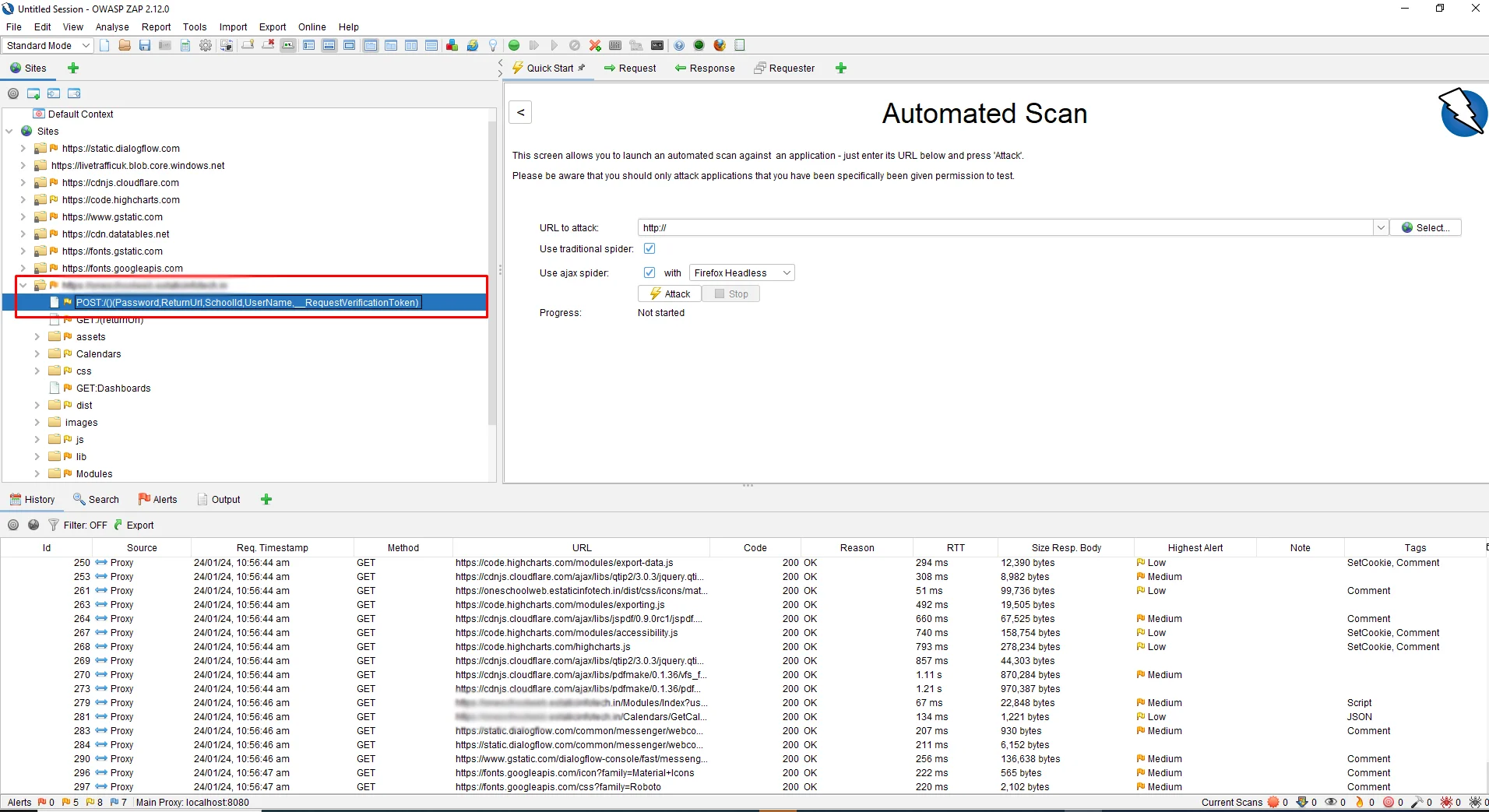
Crawl your site and log in to your site. Then, on the left side of the ZAP tool, you can see the POST URL which is a link for login authentication.
Create Context
Context: It is a method of relating a set of URLs together.
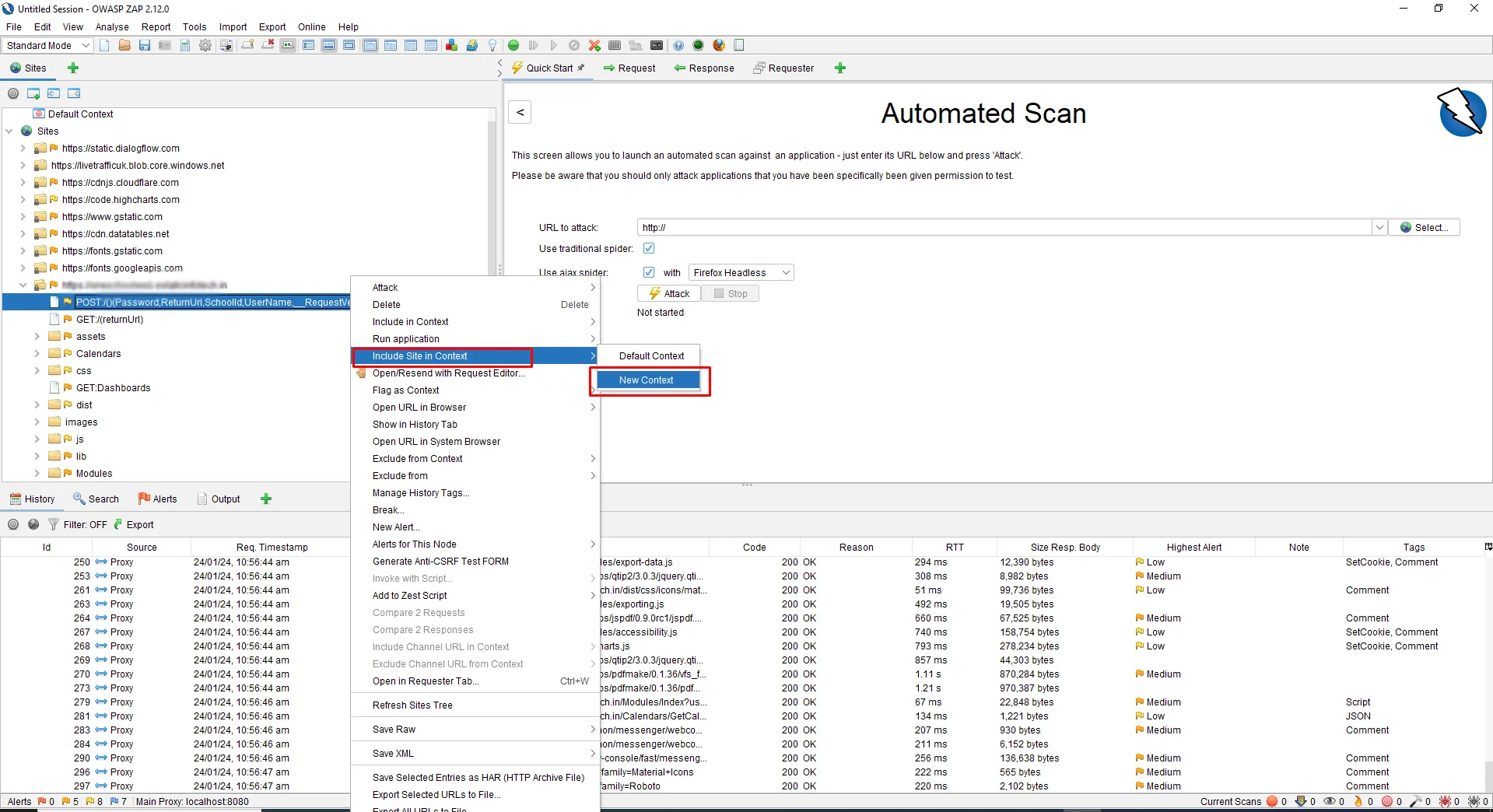
To create a new context, right-click on the Login Authentication URL and click on Include in Context -> New Context.
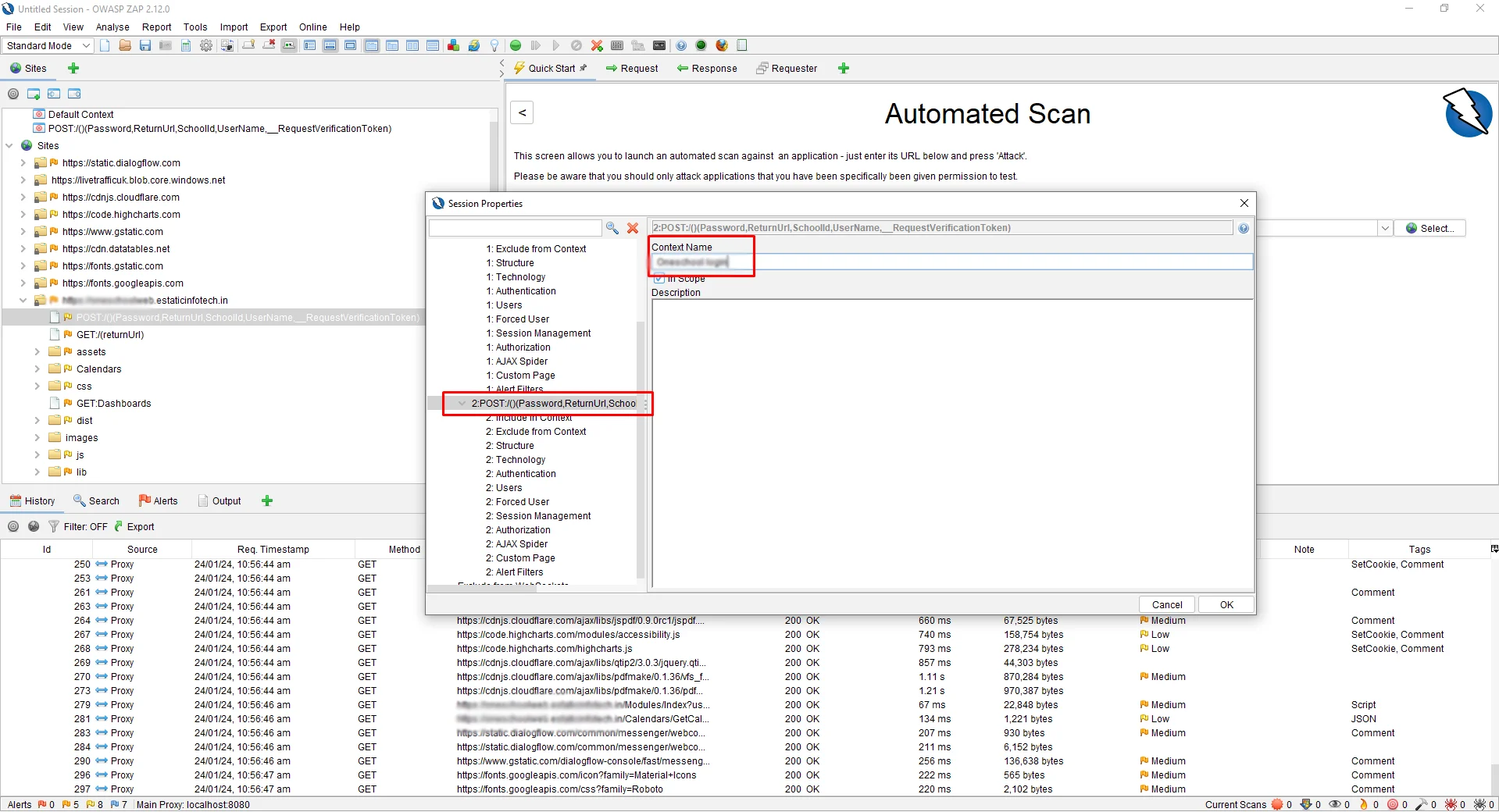
As you create a New Context, you will see another screen pop up from where you can also change the Context Name. In my case, I will change the name to “Amberis Login.” You can change the name according to your choice.
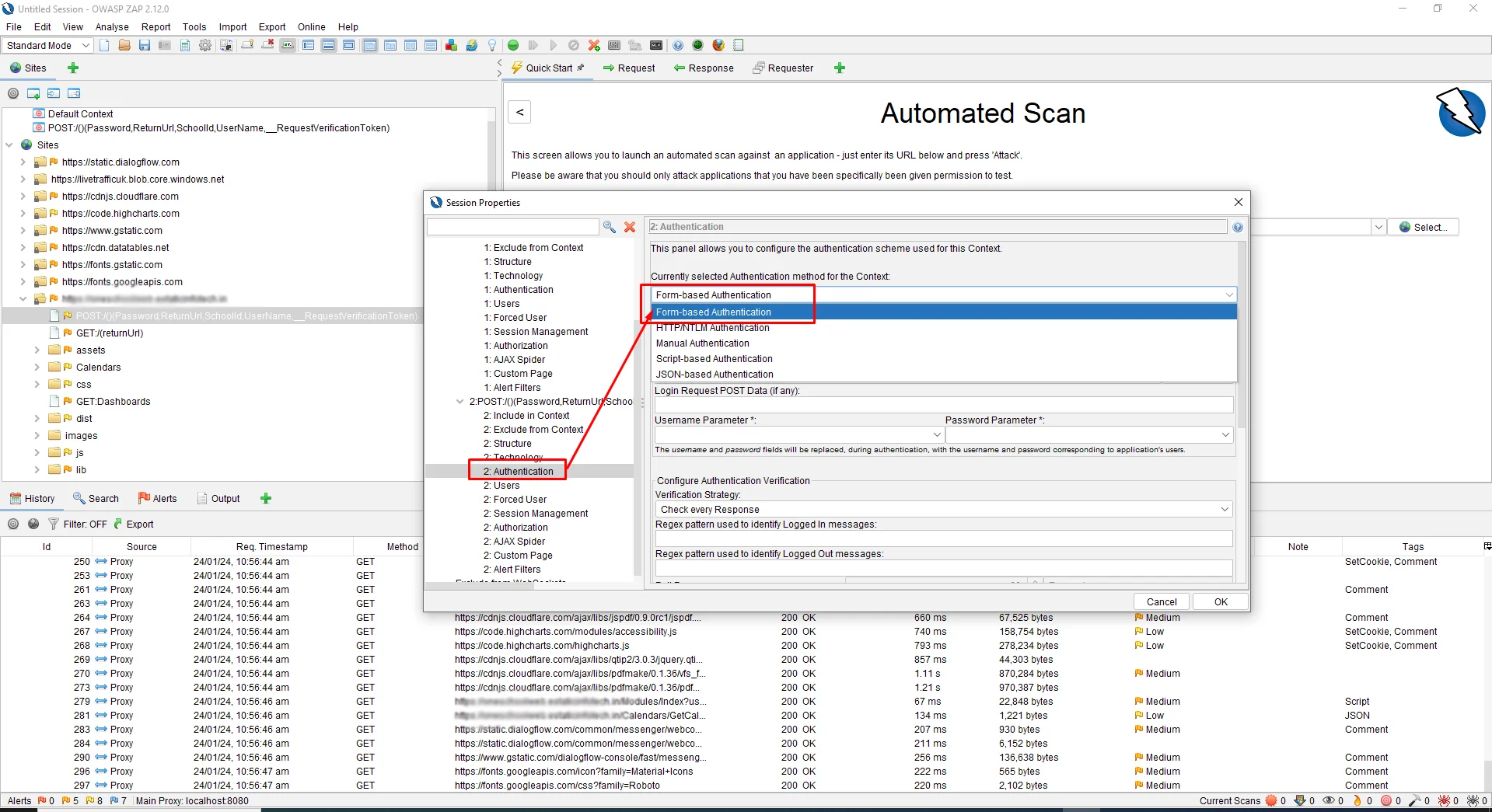
Now, click on the Authentication sub-menu, and from the Authentication drop-down select Form-Based Authentication
Then, select Login Form Target URL by clicking on the “Select” Button
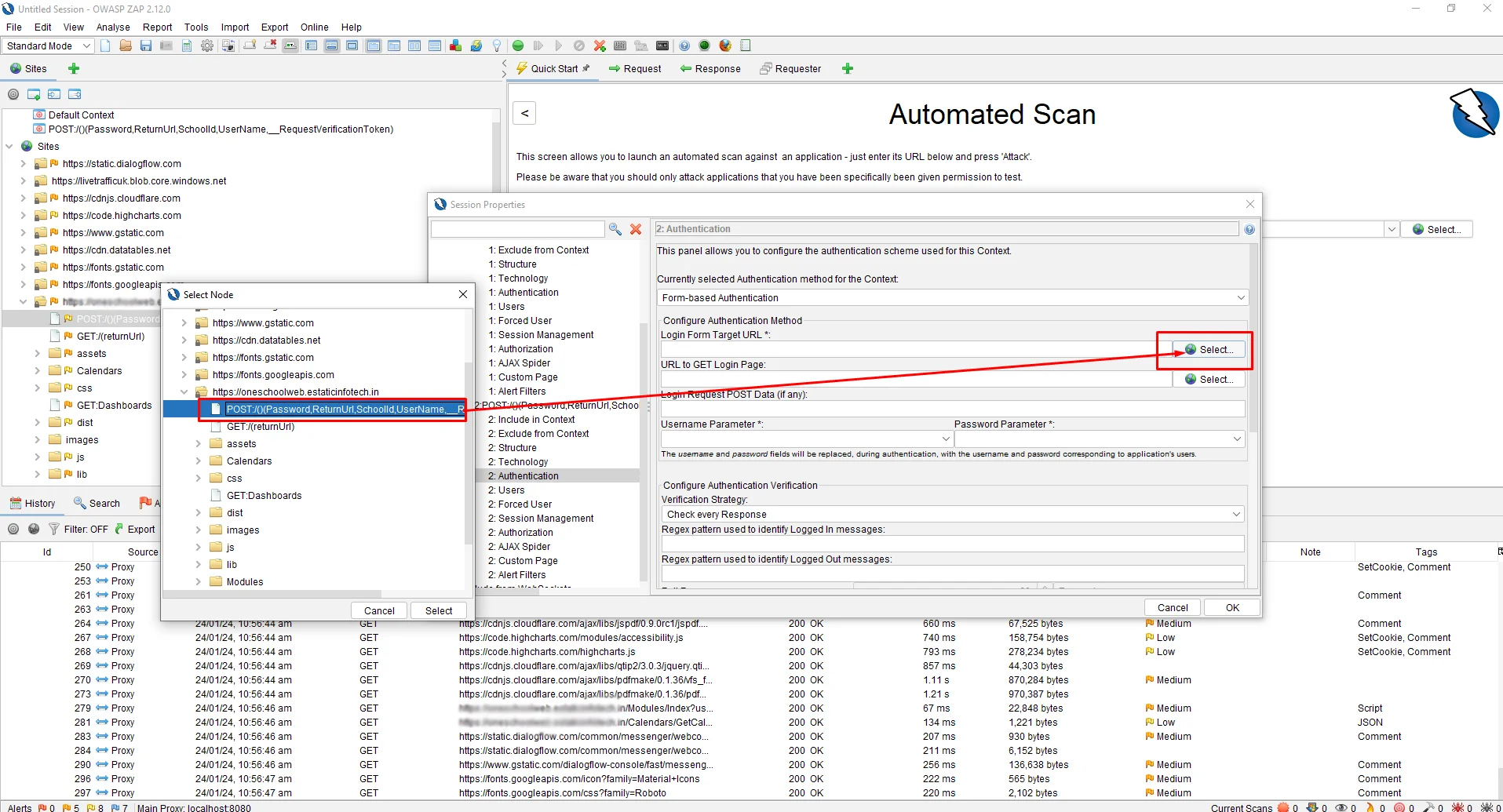
This will automatically discover the parameters we need. Now, from the username parameter drop-down, select Username.
Our Username is “User,” and our Password is “password,” which we use in the Login
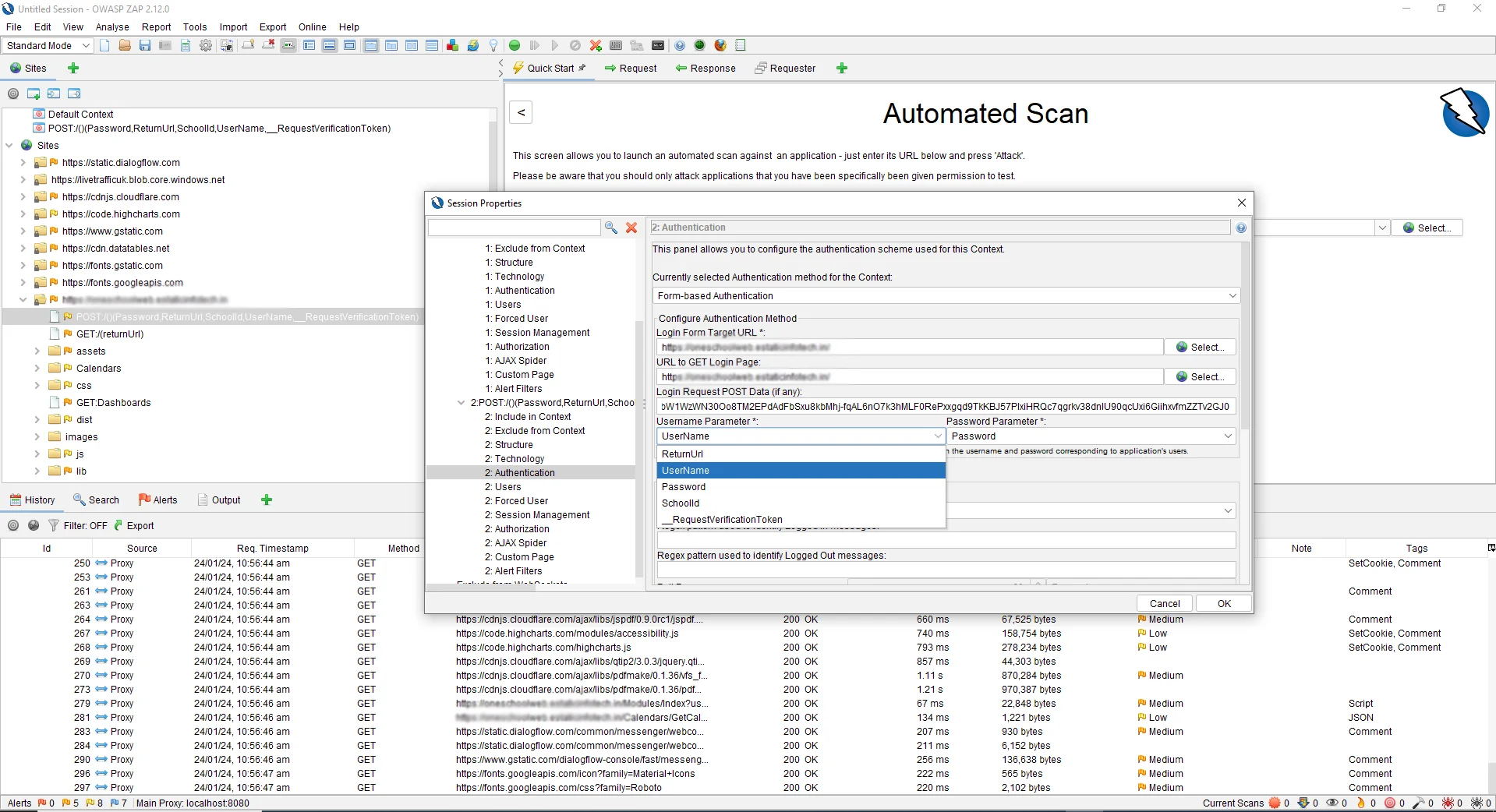
Once you are done you need to define the username and password parameter somewhere. For that, click on the Users Sub Menu. Then, click on the “Add” Button, to add a new User. In our case, I will enter my Username as “Admin.”
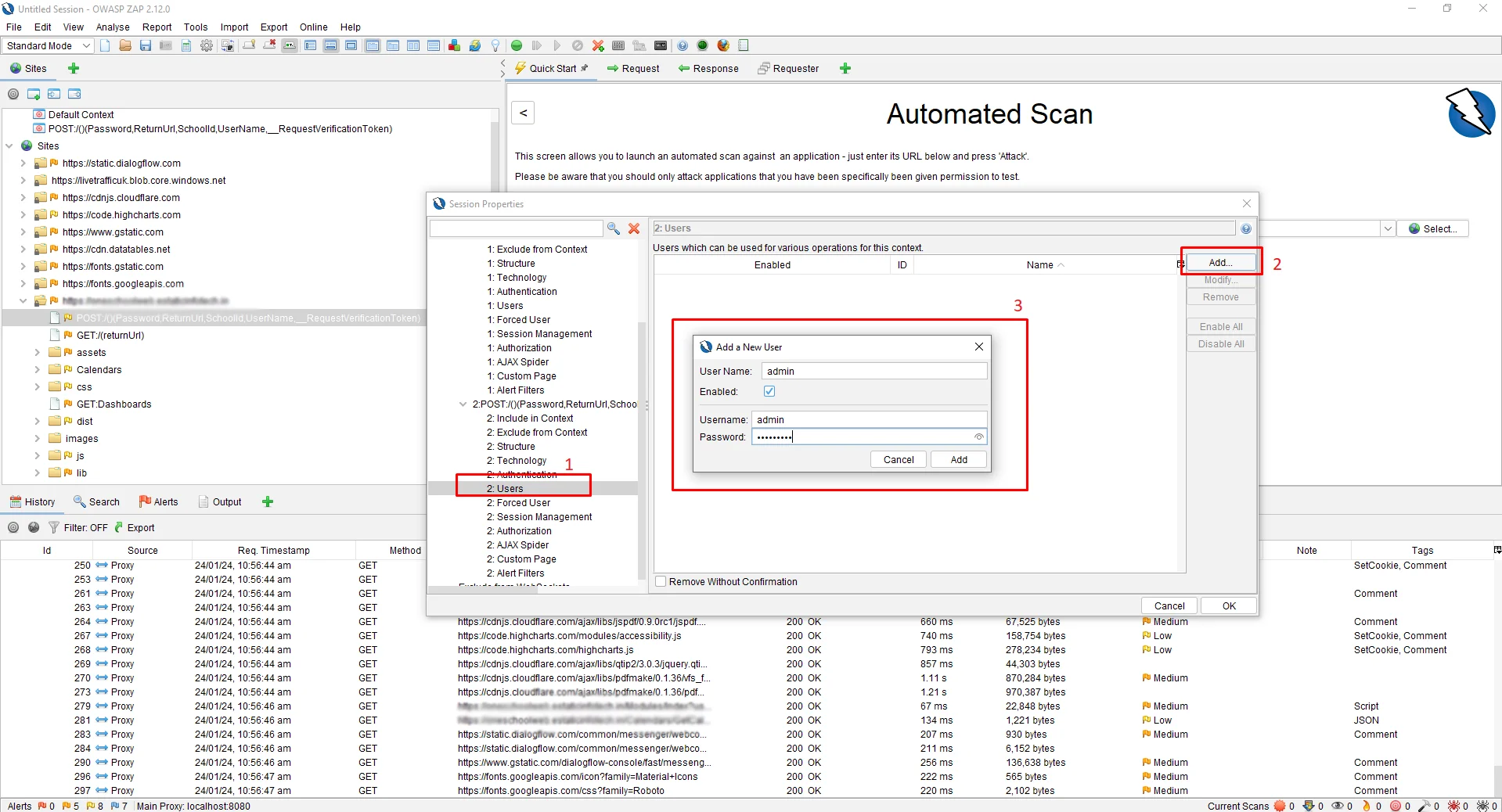
Before we start the scan, we need to set a logged-out response to let ZAP know when the application is Logged in and when it is Logged out. For that, right-click on the site login page, then click on View Page Source. Now, copy the title and paste it into the Authentication -> Logged Out Response Message text box.
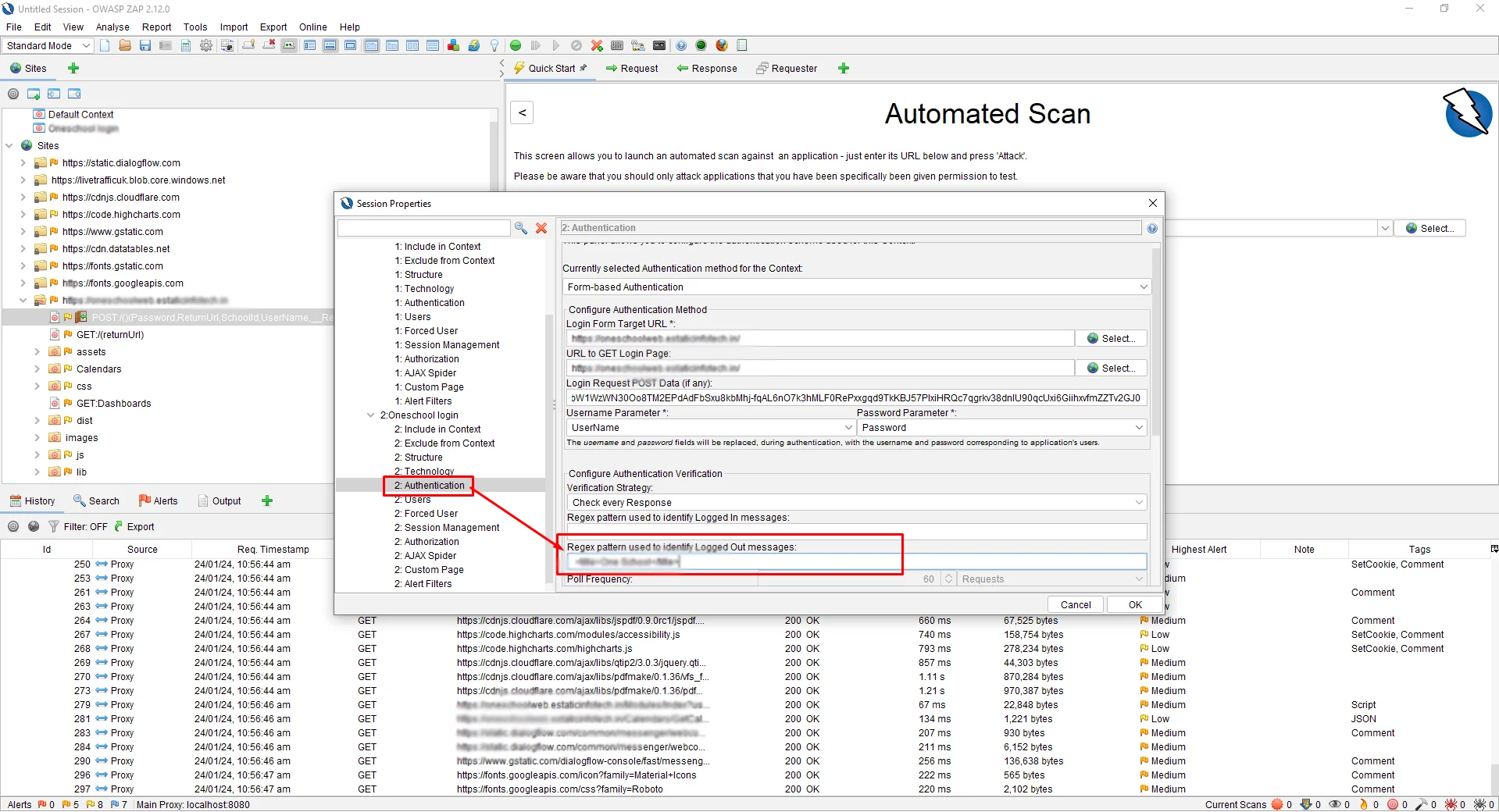
Click on the “OK” button.
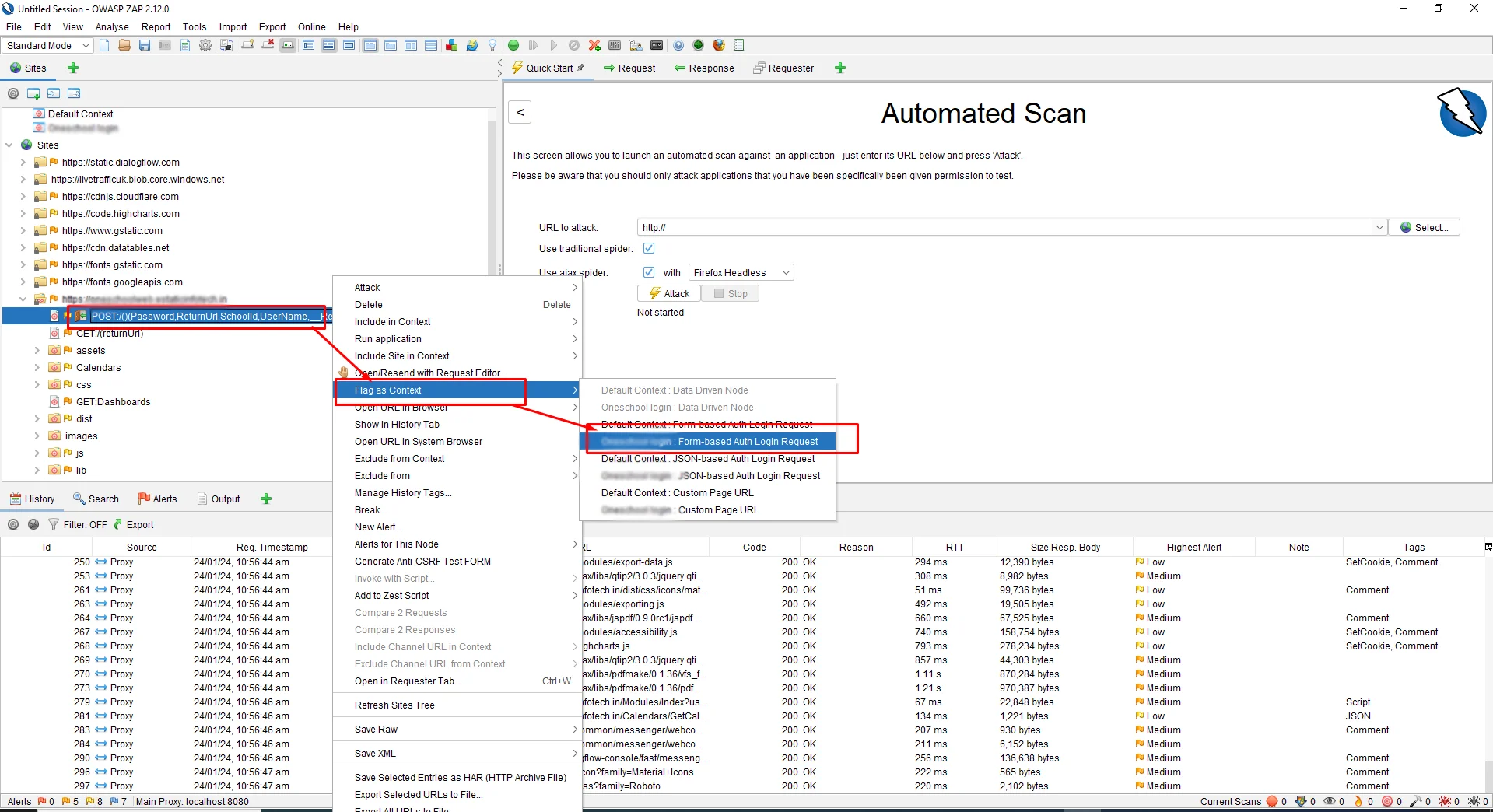
The next step is to FLAG the context we created on the POST URL. For that, follow the steps to Right-click shown in the following screenshot.
We are ready for an Authentication Scan using ZAP. But, before that, we need to make sure Forced User Mode is enabled. For that, click on the icon shown in the figure below.
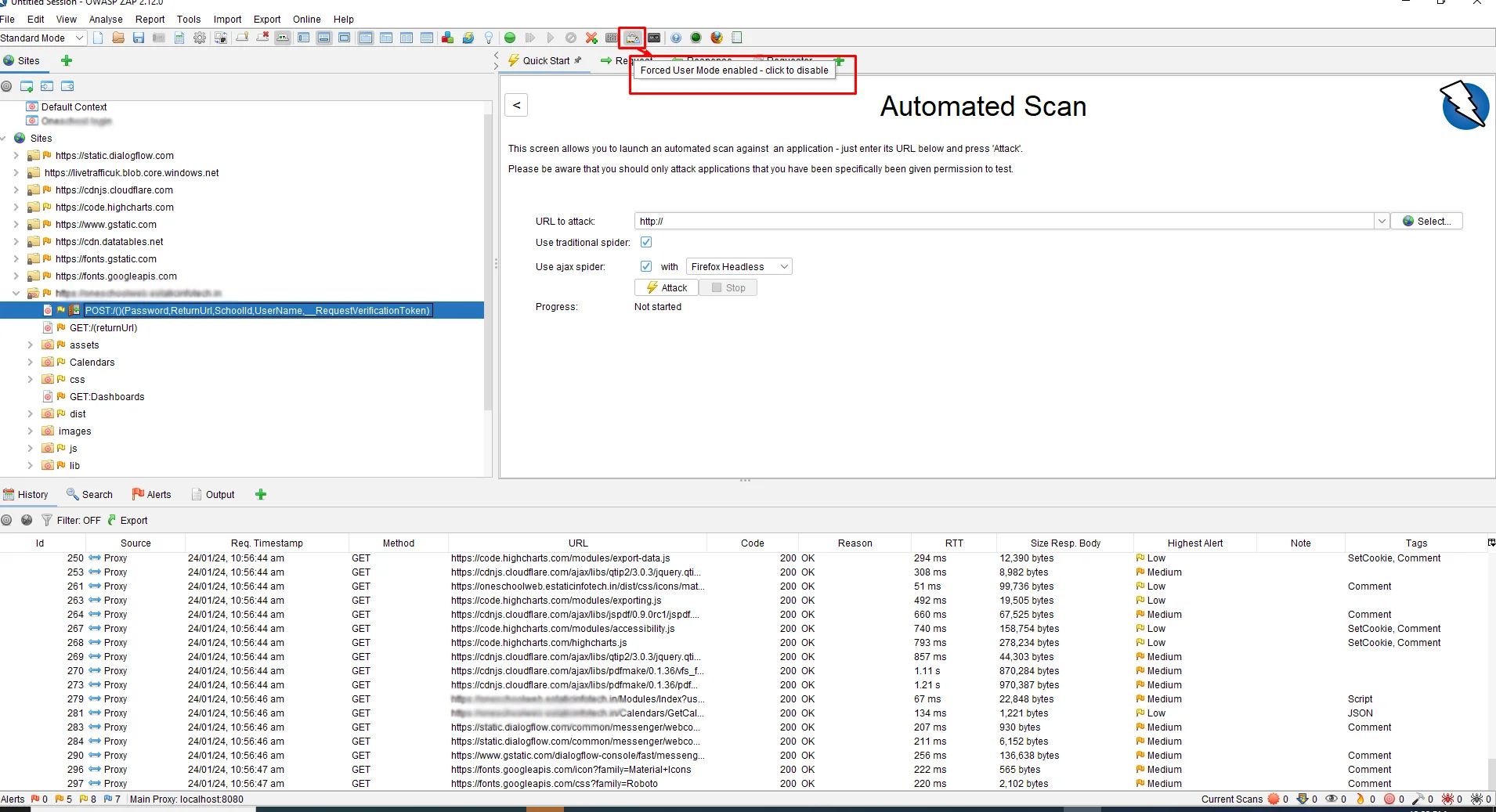
Start the Attack
Once you are done, you can now start performing the attacks by clicking on Attack -> Active Scan
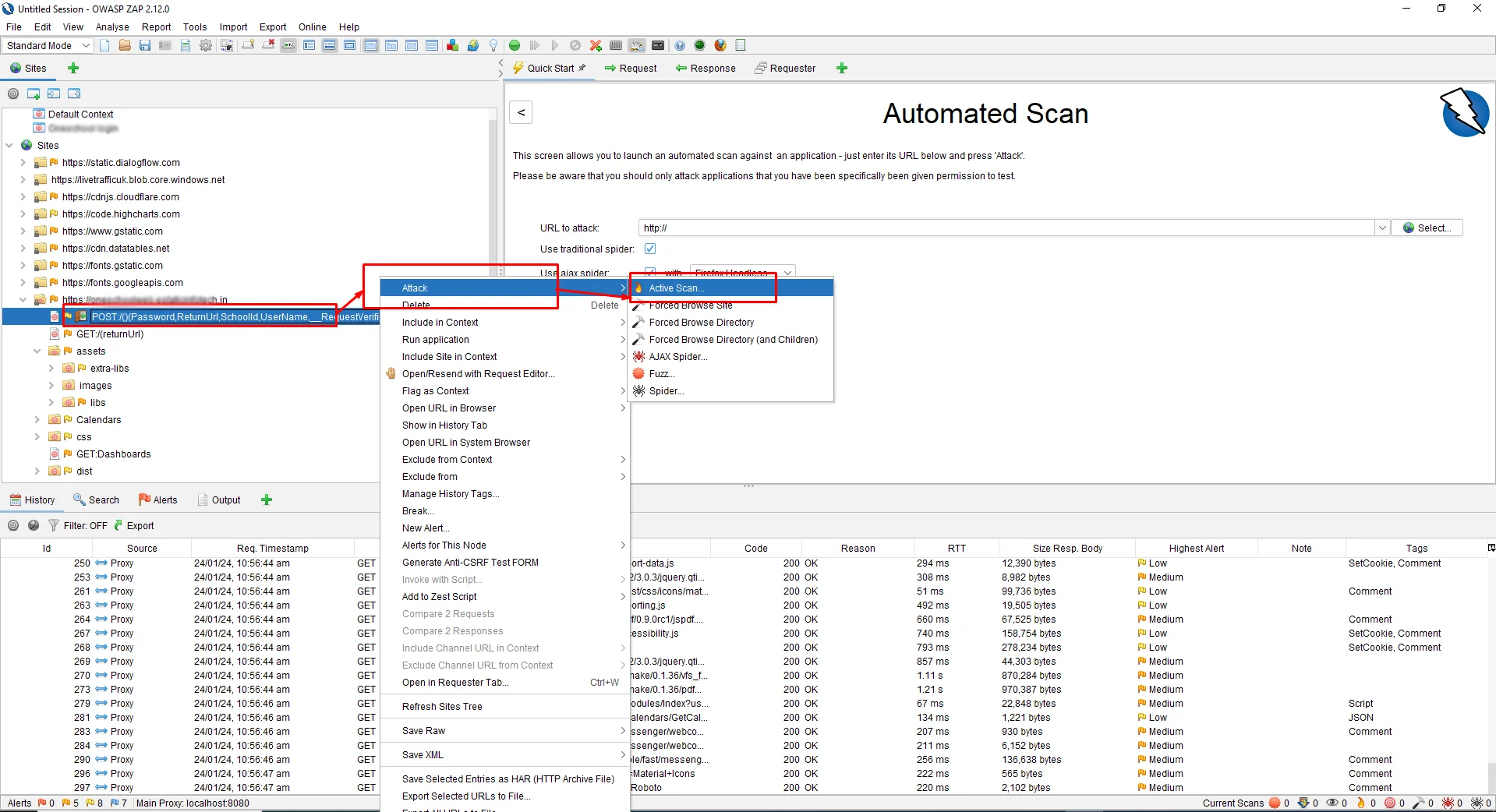
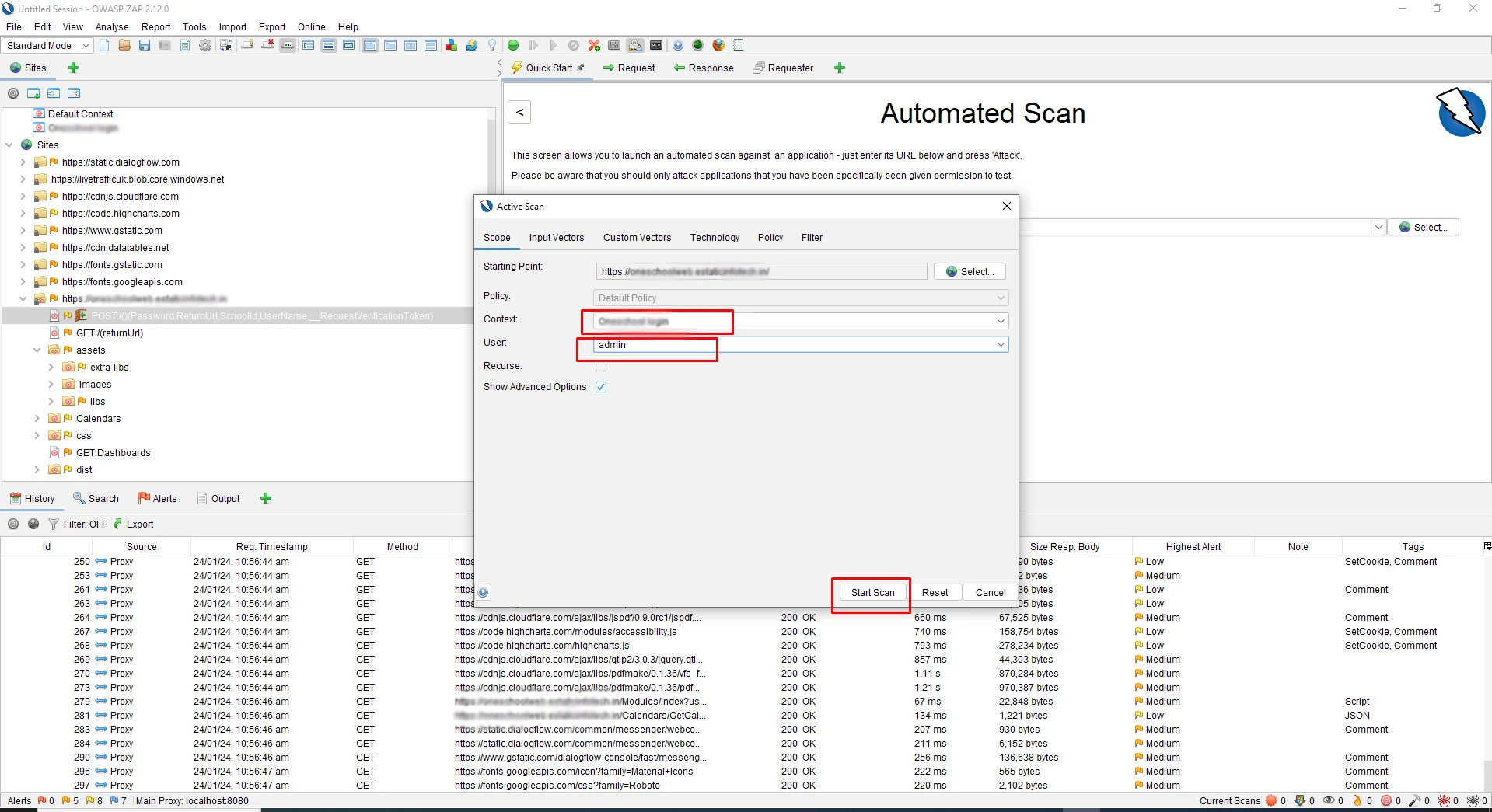
After selecting Context and User and clicking on the Start scan button the following screenshot.
This will now start performing Authenticated Scans against the application. It will try to log in to the application if it is not logged in and then discover the URLs and initiate the attacks.
Conclusion: Once the attacks are initiated, it will be alerted in the Alert Section.
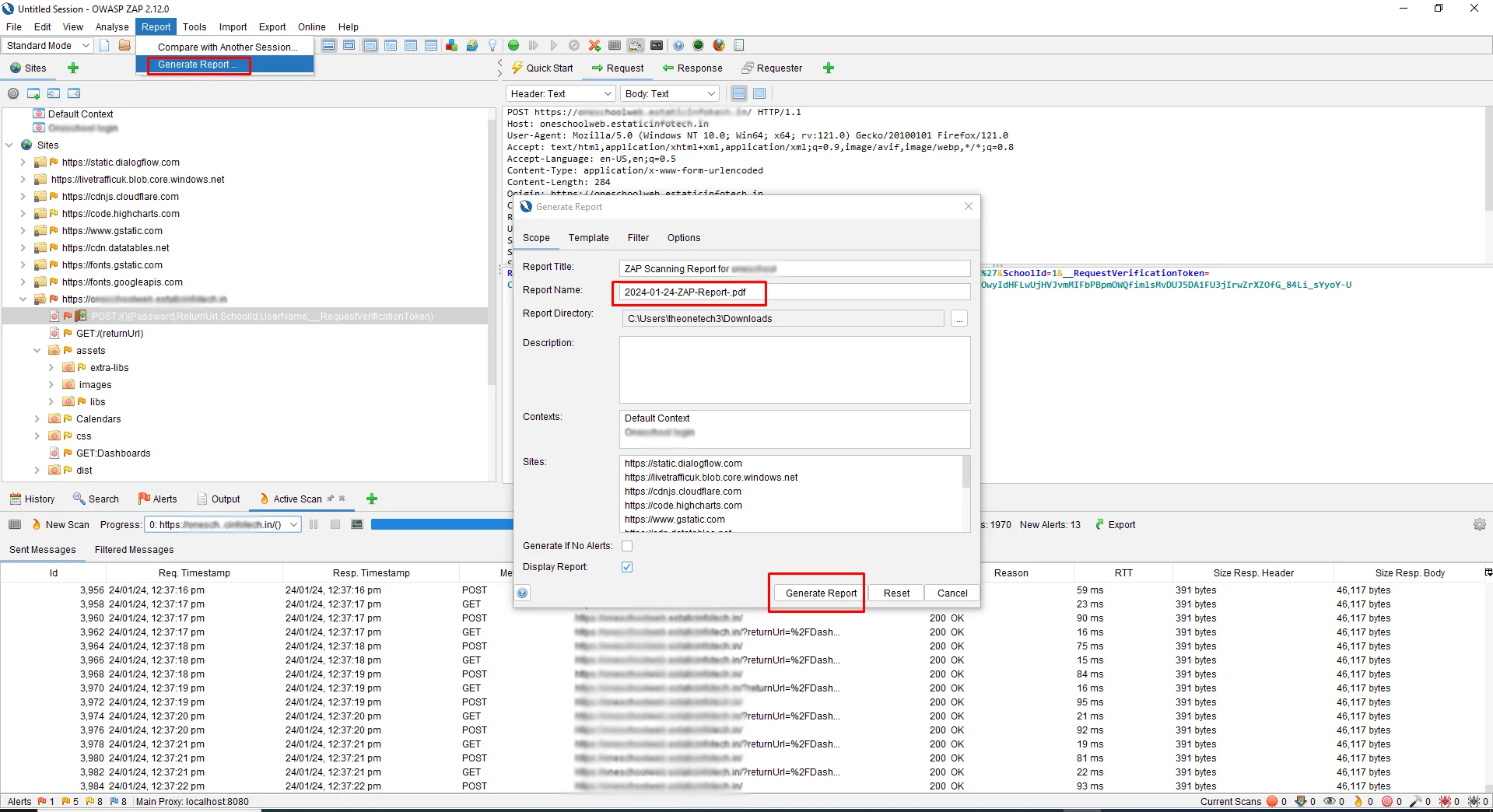
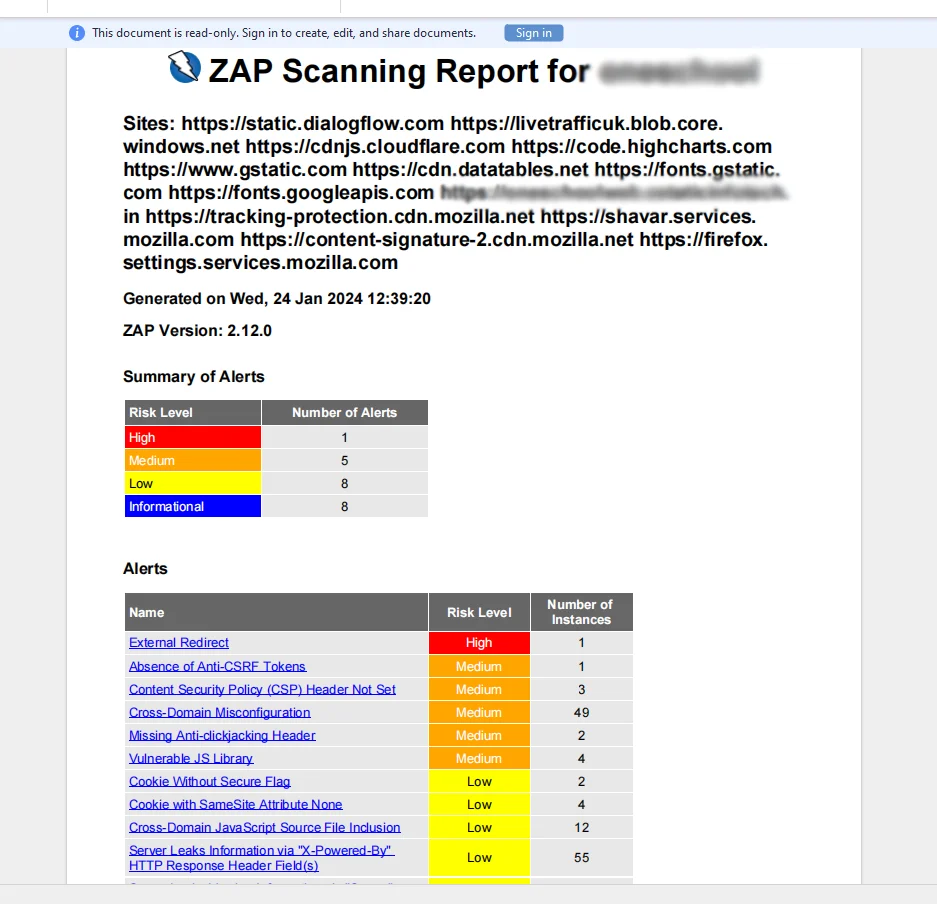
Generate Report
Click on the header of the select option of Reports -> Generate report also select the template and we can select the multiple types of the report following the below screenshot
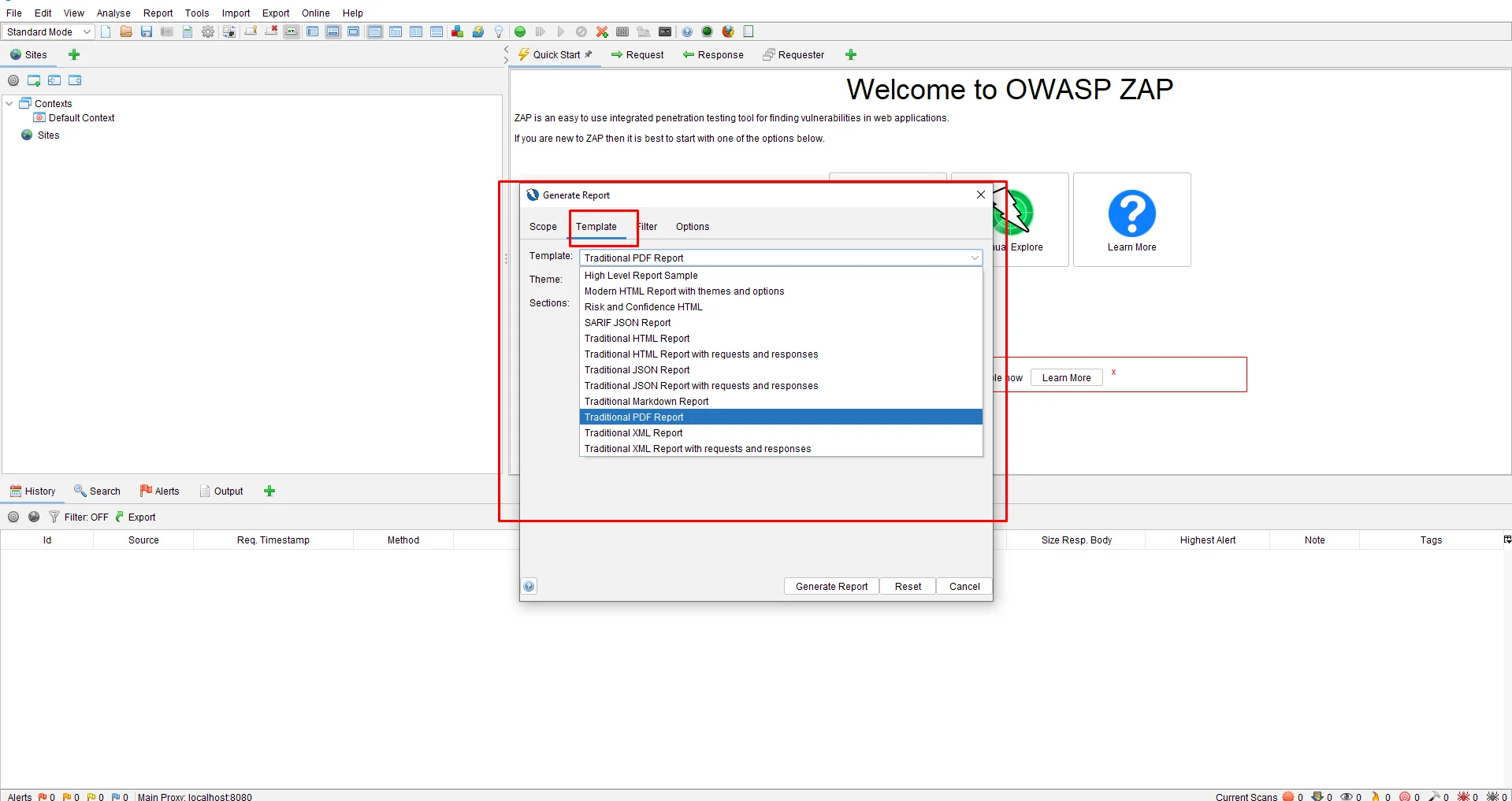
Conclusion
The necessity of comprehending and skillfully applying the several authentication techniques provided by ZAP, such as form-based, JSON-based, and script-based authentication, is emphasized in the blog post's conclusion on the dynamic process in form-based authentication with OWASP ZAP. Additionally, it would emphasize how important it is to set up correctly and run authorized scans to guarantee thorough security testing of web apps. In general, the conclusion would emphasize how important it is to have a solid understanding of authentication procedures and how to apply the right strategies to improve web applications' security posture.
About Author
Nikul Ghevariya is a dedicated QA Executive at PixelQA a Software Testing Company, evolving from a trainee to a valuable contributor across diverse projects. With ambitious goals, he aspires to master new QA tools, and delve into Automation and API testing, showcasing an unwavering commitment to continuous learning.


