Network security evaluation is an essential facet of any corporate cybersecurity approach. With the ongoing advancement and complexity of cyber threats, IT professionals are expected to be continually updated about the various aspects of network safety verification. This detailed guide delves into the significance of such evaluations, enlightening you on diverse testing methods while providing best practices formaintaining a robust and impenetrable network infrastructure. Irrespective of whether you harbor extensive experience in IT or are newly venturing into this domain, consider this guide mandatory for augmenting your comprehension regarding network security assessments.
Table of Contents
- Importance of Network Security Testing?
- Types of Network Security Testing
- Tools for Network Security Testing
- Best Practices for Conducting Network Security Testing
- Challenges and Risks of Network Security Testing
- Conclusion
Importance of Network Security Testing?
Network security testing seeks first to protect sensitive data, guarantee continuity of business operations, and maintain the image of organizations. With comprehensive security assessments performed in a timely manner, vulnerabilities in the system can be detected by IT experts, identify potential threats, and act accordingly to enforce strong security measures to prevent unauthorized log-in attempts or data breach incidents. By adopting a much more proactive approach, the assessment can determine possible flaws existing in and around the network infrastructure; it can also help to comply with mandatory certification conventions and standards.
Given the energetic nature of today's risk landscape, organizations must look for the best security testing services that adopt a proactive approach to successfully neutralize cyber threats. Kindly continue reading this document as we further explore different types of evaluation methodologies in our next section.
According to industry reports, over 70% of cyber-attacks target small businesses, highlighting the critical importance of robust network security testing and defenses for all organizations.
Types of Network Security Testing
Vulnerability Scanning
Finding potential flaws in a network's architecture proactively may be achieved through vulnerability scanning. It utilizes progressed computerized devices that systematically check network devices, applications, and frameworks to pinpoint known vulnerabilities and potential entry points for attackers. By analyzing the comes about of these filters, organizations can prioritize patches and updates to relieve dangers effectively.
Penetration Testing
Additionally referred to as ethical hacking, penetration testing surpasses vulnerability verification by simulating actual cyberattacks. This strategy includes skilled experts strategically endeavoring to exploit vulnerabilities within the network's resistance. By mimicking the strategies of pernicious on-screen characters, penetration testing gives important insights into the adequacy of security measures and the organization's capacity to resist attacks. It makes a difference in recognizing and remediating critical vulnerabilities. Recently, they can be exploited by attackers.
Security Auditing
It is an extensive evaluation of an organization's network security approaches, setups, and conventions. It guarantees compliance with predefined security measures and administrative prerequisites. Auditors audit access controls, encryption methods, firewall setups, and other security measures to recognize gaps or deviations from best practices. This process makes a difference in organizations maintaining a solid security posture and moderating potential risks.
Security Assessment
An all-encompassing method of assessing the security posture of an organization is included in the security assessment. It examines not as it were specialized viewpoints but also individuals and forms. This may include investigating security approaches and methods, conducting interviews with faculty to survey mindfulness and preparation, and evaluating physical security measures. From a broader perspective, organizations will understand vulnerabilities and weaknesses that may not be perfectly obvious with technical testing.
Using these different types of network security testing in combination will allow the organization to take steps in a proactive manner to patch its vulnerabilities and place appropriate controls to protect sensitive information and critical resources against ever-growing cyber threats.
Tools for Network Security Testing
Nmap
Nmap is also known as a network mapper and is a very commonly used open-source tool for network discovery and security audits. It allows users to find hosts and services on any network, scanning for open ports, identifying available operating systems, and performing other network tests.
Metasploit
Security personnel can use Metasploit as an effective penetration testing environment that allows them to simulate real attacks. It includes a collection of tools used for developing payloads for penetration testing across different frameworks and apps and exploiting weaknesses.
Wireshark
The Wireshark network protocol analyzer, in real-time, is capable of capturing and evaluating data packets traversing a network. It is used to investigate faults within networks, inspect the activities of a network, and hunt for abnormal behavior or security breaches.
Nessus
As a rather exhaustive tool for probing vulnerabilities, Nessus stands to make quite a difference in organizations that start to identify and remedy security loopholes on their network infrastructures. It gives computerized scans, prioritizes risks, and offers point-by-point reports to help with the moderation preparation.
Best Practices for Conducting Network Security Testing
Set Clear Testing Goals
- Define Objectives: Characterize the objectives and targets of the network security testing. This might incorporate recognizing vulnerabilities, assessing the viability of security controls, or testing incident response strategies.
- Align with Business Needs: Make sure that the testing objectives remain in accordance with the organization's risk tolerance and wider business objectives.
Understand Assessment Scope
- Define Scope: Establish the parameters of the evaluation, which include the systems, applications, and network structure that will be put to the test.
- Consider Assets: Determine which assets are essential to the organization and rank them in order of significance for testing.
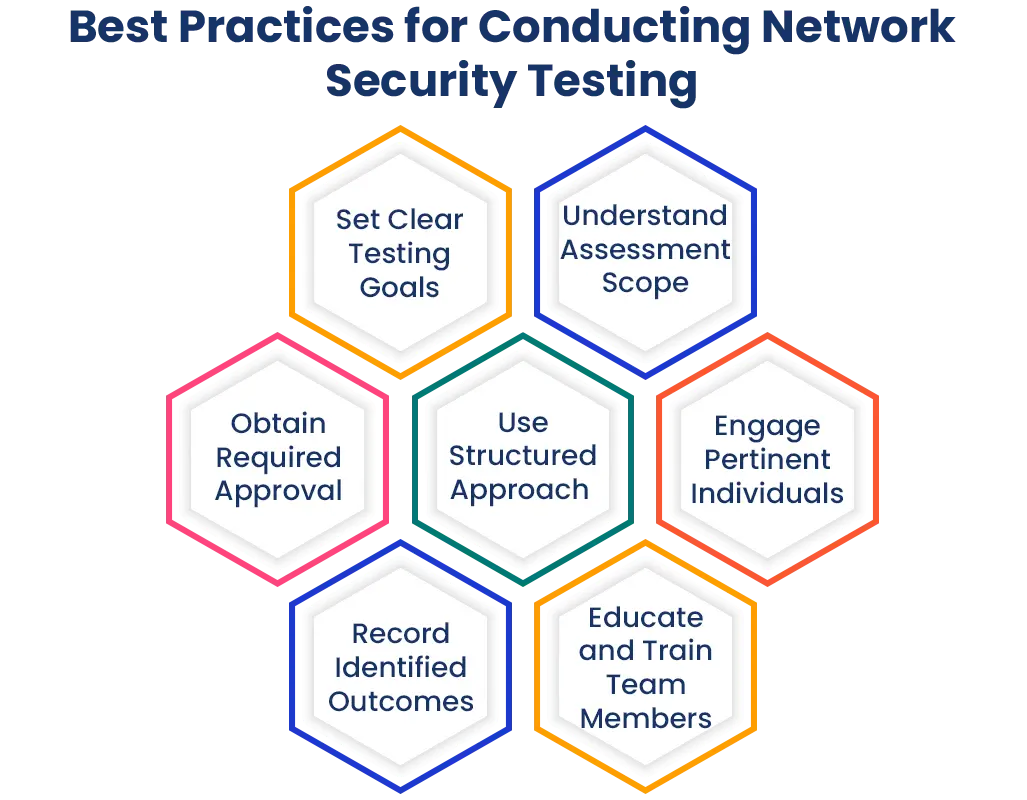
Obtain Required Approval
- Stakeholder Buy-In: Obtain approval from all relevant parties, including management, IT departments, and any other additional teams for the testing.
- Compliance and Legal Considerations: Determine that the testing tasks adhere to all applicable laws and regulations along with any relevant approvals.
Use a Structured Approach
- Regular Vulnerability Scans: To find known issues in the network infrastructure, perform regular vulnerability scans using tools like Nessus or Qualys.
- Code Reviews: To identify coding errors in security, apps, and software should have their code analyzed.
- Security Evaluations: To find and reduce prospective security vulnerabilities, conduct thorough security evaluations that should include risk assessments and penetration testing.
Engage Pertinent Individuals
- Cross-Functional Teams: Participate with personnel from other departments, such as operations, IT, security, and compliance, to ensure institutional support and all-around coverage.
- Establish Communication Channels: To efficiently deal with security threats and promote teamwork, keep lines of communication open between teams.
Record Identified Outcomes
- Document Findings: Keep track of all errors and weaknesses that have been found, along with their level of severity and potential effects they might have on the organization.
- Prioritize Remediation: Sort the discovered issues according to the degree of risk they pose, then create action plans for orderly remediation.
Educate and Train Team Members
- Awareness Programs: Conduct standard training sessions and awareness programs for IT groups and representatives to teach them about current threats, common attack vectors, and best practices for relieving risks.
- Simulated Exercises: Conduct recreated exercises, such as phishing recreations or tabletop exercises, to test the viability of security awareness training and incident response methods.
Challenges and Risks of Network Security Testing
Challenges
Coordinating Test Times
- Description: Planning the timing of network security testing to play down disruption to regular commerce activities may be a challenge. Testing during peak hours may affect critical operations.
- Impact: Disruption to business activities can lead to financial losses and affect user satisfaction.
- Proactive Measures: Schedule testing during off-peak hours or support windows to play down impact. Facilitate with significant stakeholders to ensure awareness and participation. Implement testing in separate environments to decrease the chance of disturbance.
Managing Identified Vulnerabilities
- Description: Dealing with the large number of vulnerabilities identified during testing and prioritizing them for remediation can overwhelm IT teams.
- Impact: Delays in remediation efforts can prolong exposure to potential threats, increasing the risk of exploitation.
- Proactive Measures: Categorize vulnerabilities by seriousness and prioritize based on business impact. Implement automated tools for powerlessness management to streamline the remediation process. Create clear acceleration methods for critical issues that require prompt consideration.
Verifying Effectiveness of Rectification Methods
- Description: Validating the effectiveness of chosen remediation methods can be challenging, as incorrect or ineffective measures may leave issues unresolved.
- Impact: Inadequate remediation can create new security risks or fail to address the underlying issues, leading to continued vulnerability.
- Proactive Measures: Conduct thorough testing and validation of remediation measures sometime recently before some recent Synonyms arrangement. Utilize penetration testing and validation checks to ensure that errors are viably tended to. Document and review what comes about of remediation endeavors to confirm their adequacy.
Risks
Service Interruption
- Description: During testing, there's a chance that systems can go down or have service outages, which may influence productivity and business operations.
- Consequence: User annoyance, reputational harm, and monetary losses can all arise from downtime.
- Mitigation: Communicate any possible development disruptions and properly plan testing procedures. If problems arise during testing, have procedures in place for rolling back changes to quickly restore services.
Neglect of Important Vulnerabilities
- Description: It is possible for crucial flaws to be uncovered during testing, which could expose the network to potential attacker exploitation.
- Consequence: Neglecting important vulnerabilities may result in security incidents, illegal access, or data breaches.
- Mitigation: To identify and mitigate every possible security risk, employ thorough testing methods such as penetration testing and thorough checks. Make that all network components including third-party frameworks and apps are tested.
Inadequate Protection of Confidential Data
- Description: Data breaches or compliance problems may arise if private or sensitive data is not sufficiently protected during testing.
- Consequence: Exposure of confidential information may lead to financial penalties, legal consequences, regulatory actions, and reputational harm to the company.
- Mitigation: Use suitable information handling protocols and, when feasible, use sanitized or anonymized data for testing. Make sure that sensitive data is encrypted or secured while conducting tests.
Conclusion
A thorough cybersecurity strategy must include network security evaluation. Through a methodical evaluation and enhancement of their network infrastructure security, establishments can augment the protection of their information, systems, and resources from cyber hazards. So, invest in your cybersecurity with confidence by hiring a reputable software testing company like PixelQA to conduct extensive network security evaluations and fortify your defenses against cyber threats.
About Author
Started his journey as a software tester in 2020, Rahul Patel has progressed to the position of Associate QA Team Lead" at PixelQA.
He intends to take on more responsibilities and leadership roles and wants to stay at the forefront by adapting to the latest QA and testing practices.


