
How QA Ensures Robust Data Protection Across Software Systems
Stop data breaches before they start. Learn how a security-focused QA process is your first line of defense, ensuring compliance and building unbreakable user trust.

Cryptocurrency App Testing: What QA Teams Need to Know
A single bug can be devastating. Discover the essential security, performance, and compliance testing strategies for future-proof cryptocurrency applications.

Crypto App QA: Top Challenges and Solutions for Blockchain Quality
One flaw can cost millions. Discover the essential QA practices for smart contract auditing, managing security vulnerabilities, and ensuring data integrity in crypto applications.

Top Vulnerabilities Found in Web and Mobile Apps – and How QA Helps
Explore the 7 major web and mobile app vulnerabilities (XSS, SQL Injection, Insecure Data Storage). Understand the business case for QA in securing your applications.

Understanding Vulnerability Assessment: Tools, Techniques, and Benefits
Protect your organization from data breaches and cyber attacks. Explore the tools, techniques, and business benefits of a comprehensive vulnerability assessment.

Why Your Business Can’t Afford to Skip Network Security Testing
Network security testing isn't optional—it's essential. Learn why testing is your best defense against breaches, downtime, and lost trust.

A Step-by-Step Guide to Network Security Testing for Enterprises
Learn how to secure your enterprise network with this step-by-step guide. From vulnerability scans to pen testing—practical advice, no jargon.
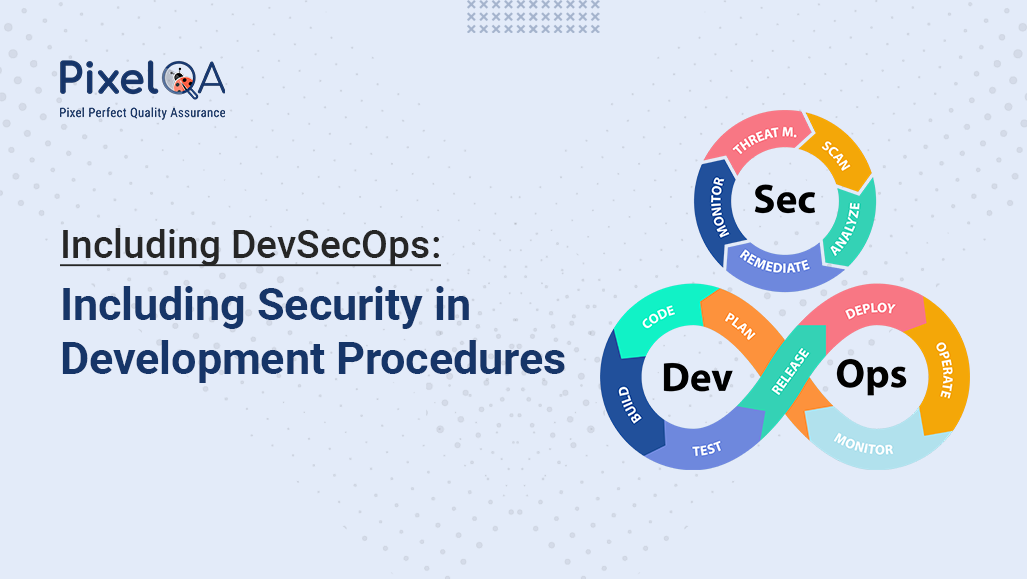
Including DevSecOps: Including Security in Development Procedures
Learn how DevSecOps embeds security into every phase of the software development lifecycle. Discover its benefits, challenges, tools, and best practices for secure and faster development.
