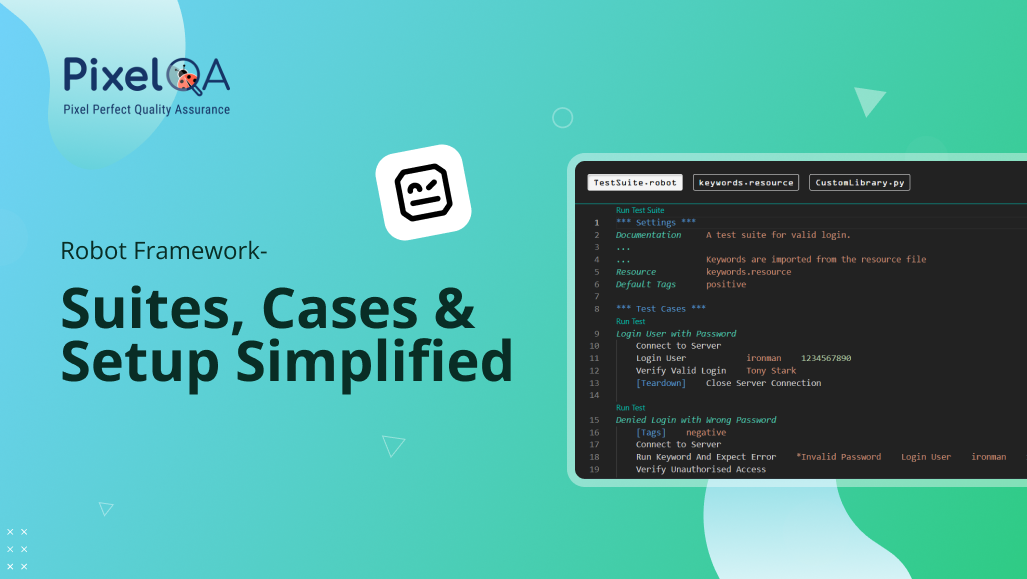
Robot Framework- Suites, Cases & Setup Simplified
Learn how to simplify test automation using Robot Framework. Understand how to create test suites, define cases, and streamline setup for efficient QA workflows.

Automation Testing for Legacy Software:- How to Modernize QA Processes
Modernize QA for legacy software with automation. Learn key challenges, tools, and steps to streamline testing, reduce risks, and boost release speed.

Uncover Hidden Security Risks with Expert Penetration Testing Company
Learn how penetration testing companies like PixelQA identify vulnerabilities before hackers do, using advanced tools and real-world tactics.

Penetration Testing: Your First Line of Cyber Defense
Hiring a penetration testing company now could save you millions later. See why it’s essential for modern businesses to gear up before they are attacked.

How AI Is Transforming Software Testing & Quality Assurance
Explore how AI is revolutionizing software testing. From smart automation to predictive defect detection, see what it means for the future of QA professionals.

Will AI Replace Human Testers? Exploring the Future of QA
Can AI replace human testers? Discover how AI enhances software testing, its limits, and why human insight remains essential in the QA landscape.

Preparing for APTs: The Power of APT Simulation Testing
Learn how APT simulation testing helps detect, prevent, and respond to covert cyberattacks. Discover tools, benefits, and best practices to stay protected.

Ensuring Bug-Free Software: How QA Experts Deliver Quality Releases
Discover how leading QA companies like PixelQA help clients release stable, secure, and scalable software through proven quality assurance methodologies.
